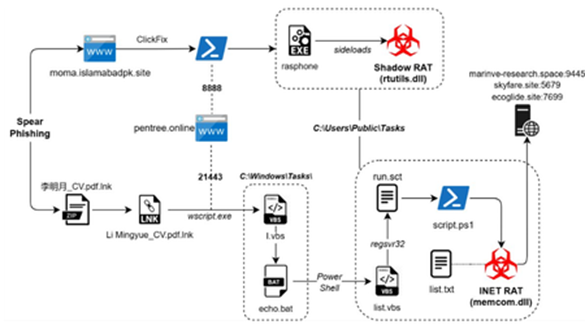
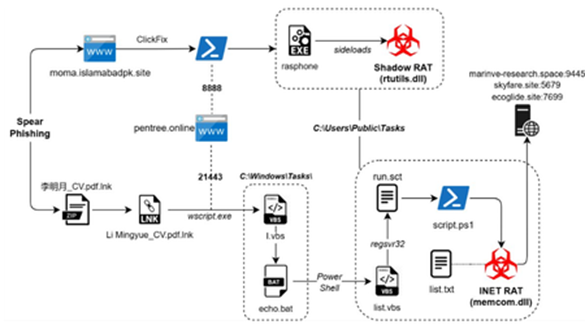
Virtual Private Networks (VPNs) have been the go-to solution for securing remote access to banking systems for decades. They created encrypted tunnels for employees, vendors, and auditors to connect with core banking applications. But as cyber threats become more sophisticated, regulatory bodies tighten their grip, and branch operations spread into rural areas, it becomes increasingly clear that VPNs are no longer sufficient for regional and cooperative banks in India.
The Cybersecurity Reality for Banks
The numbers speak for themselves:
- In just 10 months of 2023, Indian banks faced 13 lakh cyberattacks, averaging 4,400 daily.
- Over the last five years, banks reported 248 successful data breaches.
- In the first half of 2025 alone, the RBI imposed ₹15.63 crore in penalties on cooperative banks for compliance failures, many linked to weak cybersecurity practices.
The most concerning factor is that most of these incidents were linked to unauthorized access. With their flat network access model, traditional VPNs make banks highly vulnerable when even one compromised credential slips into the wrong hands.
Why VPNs Are No Longer Enough
- Over-Privileged Access
VPNs were built to provide broad network connectivity. Once logged in, users often gain excessive access to applications and systems beyond their role. This “all-or-nothing” model increases the risk of insider threats and lateral movement by attackers.
VPNs were built to provide broad network connectivity. Once logged in, users often gain excessive access to applications and systems beyond their roles.
- Lack of Granularity
Banks require strict control over who accesses what. VPNs cannot enforce role-based or context-aware access controls. For example, an external auditor should only be able to view specific reports, not navigate through the entire network.
- Operational Complexity
VPN infrastructure is cumbersome to deploy and maintain across hundreds of branches. The overhead of managing configurations, licenses, and updates adds strain to already stretched IT teams in regional banks.
- Poor Fit for Hybrid and Remote Work
Banking operations are no longer confined to branch premises. Remote staff, vendors, and regulators need secure but seamless access. VPNs slow down connectivity, especially in rural low-bandwidth areas, hampering productivity.
- Audit and Compliance Gaps
VPNs don’t inherently provide built-in audit logs, geo-restriction policies, or continuous verification—making compliance audits more painful and penalties more likely.
The Rise of Zero Trust Network Access (ZTNA)
Zero Trust Network Access (ZTNA) addresses the shortcomings of VPNs by adopting a “never trust, always verify” mindset. Every user, device, and context is continuously authenticated before and during access. Instead of broad tunnels, ZTNA grants access only to the specific application or service a user is authorized for—nothing more.
For regional and cooperative banks, this shift is a game-changer:
- Least-Privilege Access ensures employees, vendors, and auditors only see what they can.
- Built-in Audit Trails support RBI inspections without manual effort.
- Agentless Options allow quick deployment across diverse user groups.
- Resilience in Low-Bandwidth Environments ensures rural branches stay secure without connectivity struggles.
Seqrite ZTNA: Tailored for Banks
Unlike generic ZTNA solutions, Seqrite ZTNA has been designed with India’s banking landscape in mind. It supports various applications, including core banking systems, RDP, SSH, ERP, and CRM, while seamlessly integrating with existing IT infrastructure.
Key differentiators include:
- Support for Thick Clients, such as core banking and ERP systems, is critical for cooperative banks.
- Out-of-the-Box SaaS Support for modern banking applications.
- Centralized Policy Control to simplify access across branches, vendors, and staff.
In fact, a cooperative bank in Western Maharashtra replaced its legacy VPN with Seqrite ZTNA and immediately reduced its security risks. By implementing granular, identity-based access policies, the bank achieved secure branch connectivity, simplified audits, and stronger resilience against unauthorized access.
The Way Forward
The RBI has already stated that cybersecurity resilience will depend on zero-trust approaches. Cooperative and regional banks that continue to rely on legacy VPNs are exposing themselves to cyber risks, regulatory penalties, and operational inefficiencies.
By moving from VPNs to ZTNA, banks can protect their sensitive data, secure their branches and remote workforce, and stay one step ahead of attackers—all while ensuring compliance.
Legacy VPNs are relics of the past. The future of secure banking access is Zero Trust.
Secure your bank’s core systems with Seqrite ZTNA, which is built for India’s cooperative and regional banks to replace risky VPNs with identity-based, least-privilege access. Stay compliant, simplify audits, and secure every branch with Zero Trust.