I’m Bimo Tri, a multidisciplinary designer and creative developer based in Indonesia. I run a small independent studio called Studio•Bämo.J®, working between Jakarta and Bali — or pretty much anywhere I can find a fast internet connection.
My focus is on building expressive digital experiences, mostly portfolio sites and brand platforms for creatives, studios, and design-forward brands. With roots in both design and development, I enjoy blending visual precision with motion and interactivity to create work that feels both thoughtful and visceral. I care deeply about craft, story, and making things that resonate beyond just visuals.
Showcase
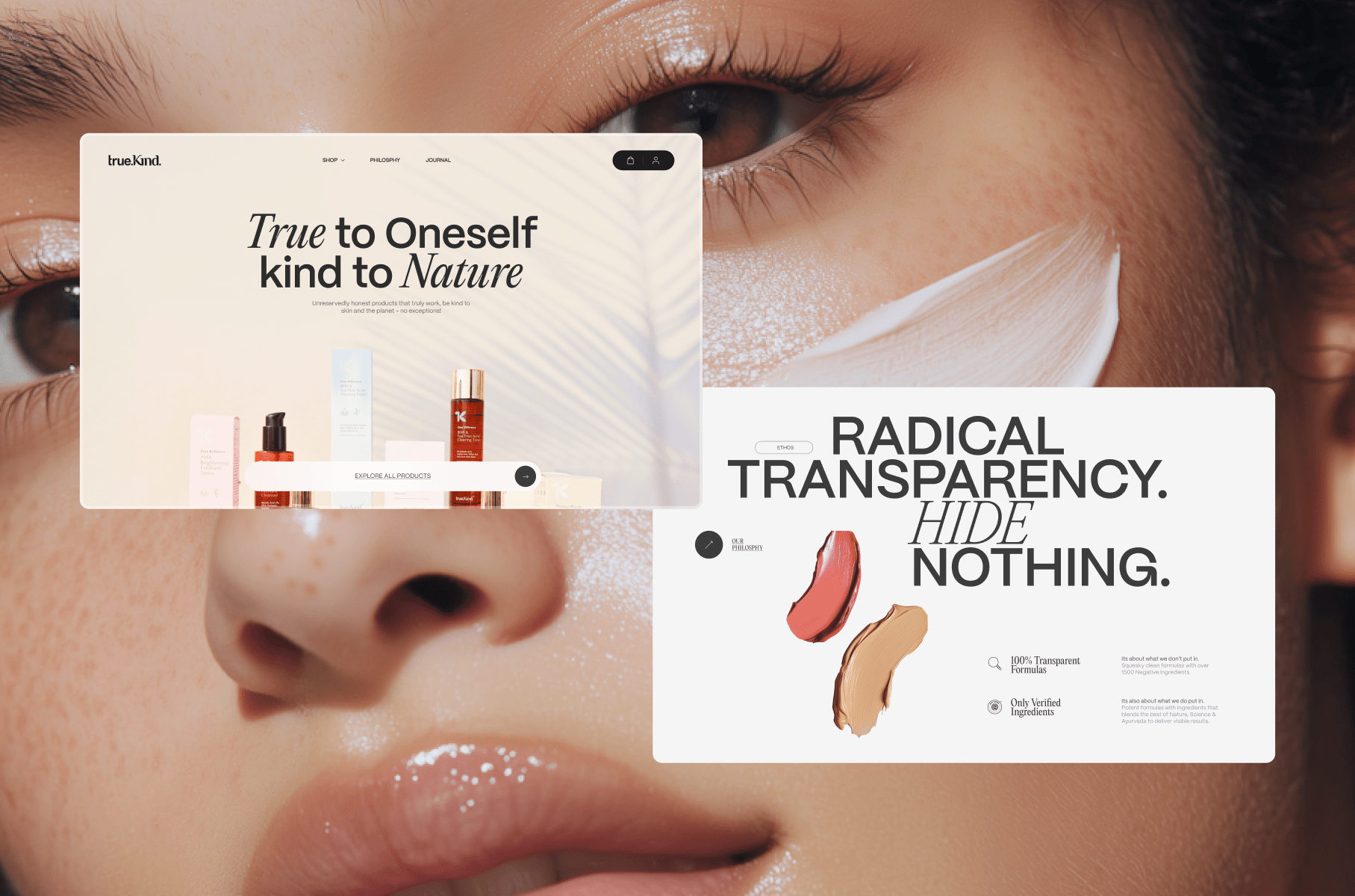
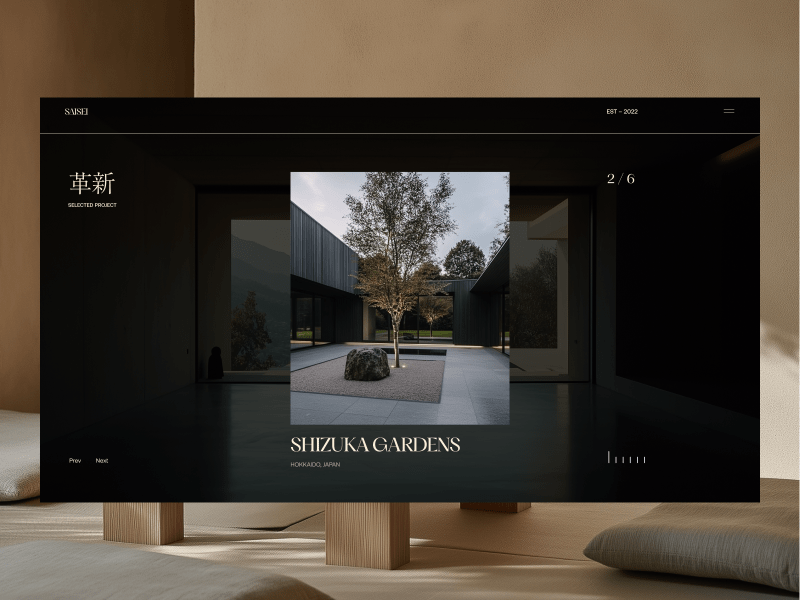
SAISEI
Saisei is a visionary architecture firm based in Tokyo, Japan, focused on sustainability, culture, and timeless design. I designed and developed the site to reflect their philosophy merging traditional Japanese aesthetics with clean, contemporary digital design.



Achievements
This project was a major milestone in my career. It brought home my first Awwwards Site of the Day and earned recognition from several other platforms. The positive feedback from the design community affirmed my approach to cultural storytelling through digital mediums.
Personal notes
Saisei remains one of my favorite works. I’ve always been drawn to the tension between heritage and modernity, and this project gave me the space to explore that deeply. The recognition it received made the process even more meaningful.
Live Site Link: https://saisei-sbj.webflow.io/
NĀGARA
Nagara is a concept project developed in collaboration with my buddy Felixander Yuan, created as part of the #DareToShare24 design challenge by @bentenwordring.
It reimagines a luxury watch brand that fuses the precision of Swiss watchmaking with the cultural depth of the Majapahit Empire. Each timepiece acts as a tribute not just to technical craftsmanship, but to historical richness and aesthetic symbolism rooted in Indonesian heritage.





Challenges
One of the biggest hurdles was exploring AI-generated imagery and motion assets. Using tools like Midjourney and Kling, it took numerous iterations to dial in a visual direction that felt both on-brand and high-end. Getting the product visuals — especially the watches — to look authentic and aligned with the brand’s narrative was far more challenging than anticipated.
Achievements
The final result was a fully animated concept site that we were genuinely proud of. Yuan did an amazing job bringing the dev and motion to life. Beyond that, the project ended up winning the monthly challenge, earning recognition and some cool prizes — a nice bonus on top of the creative satisfaction.
Personal notes
This one felt personal. The month’s theme was “Luxury” — a space I naturally gravitate toward — and we were allowed to team up for the final challenge. I chose to work with Yuan, someone I’ve respected and known for a while. The entire process felt like a return to roots — storytelling, culture, and collaboration — wrapped inside a luxury narrative.
Live Site Link: https://nagara-daretoshare.webflow.io/
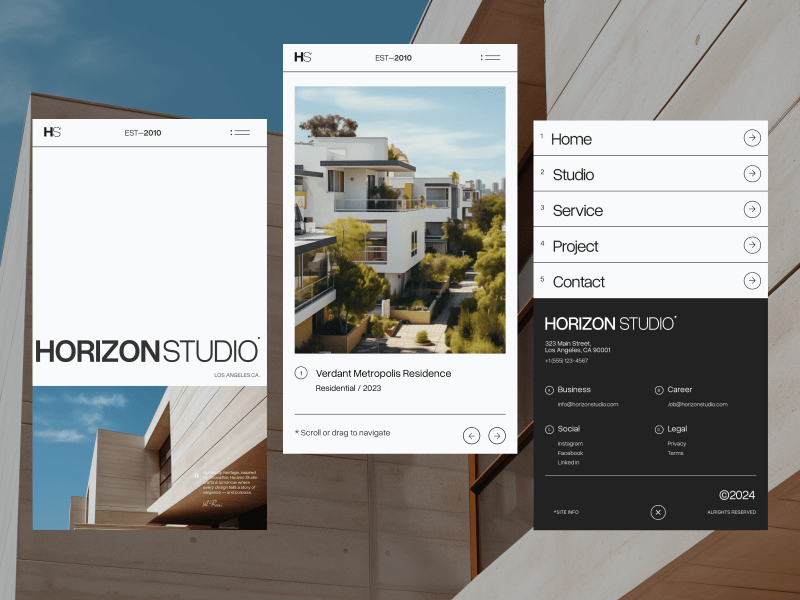
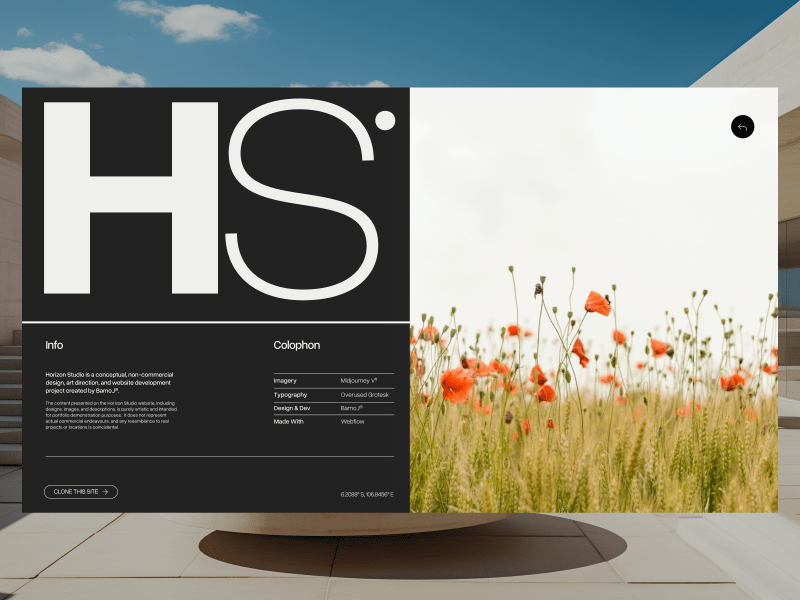
HorizonStudio
Horizon Studio is a conceptual architecture firm based in Los Angeles, created to explore the intersection of art, design, and technology. Inspired by my love for architecture and interior design, the site showcases sleek, avant-garde visuals with a focus on sustainability. I used Midjourney for the visual assets and GPT to shape the narrative, crafting an experience that feels modern and immersive.



Achievements
The site received an Honorable Mention from Awwwards — a validating moment for me as it was one of my earliest forays into the architecture space. The feedback highlighted the strength of the design direction and the site’s overall atmosphere.
Personal notes
This was the first project where I went all in with generative AI — every asset was made using prompts, and honestly, it was pretty sloppy at first. But through experimentation, I managed to create a cohesive visual style that looked like it came from one photographer. It reminded me how fun it is to dive into the unknown and just explore.
Live Site Link: https://horizonstudioarchitecture.webflow.io/
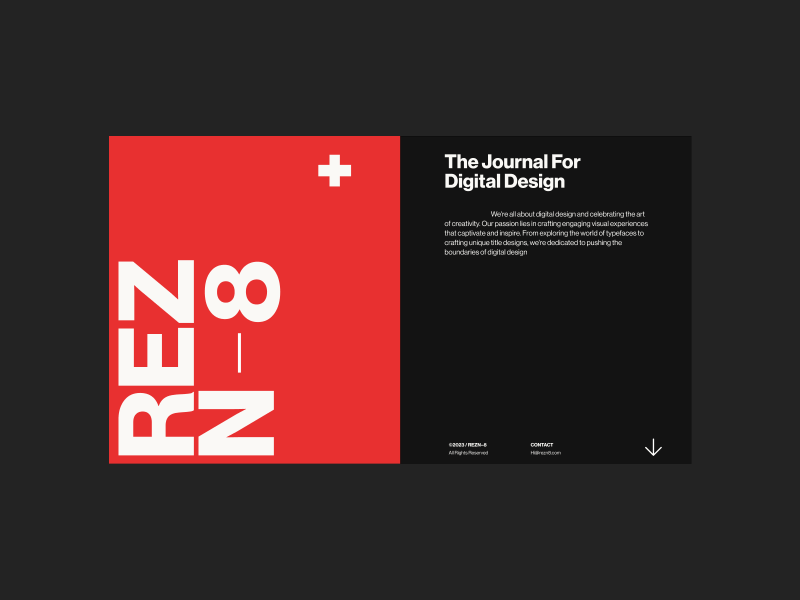
REZN-8

REZN-8 is a typographic and layout exploration rooted in Swiss design principles. It started as a poster experiment and evolved into a full website — my first time building a motion-heavy site entirely with code. It was all about translating static design into something dynamic, expressive, and functional in a digital format.




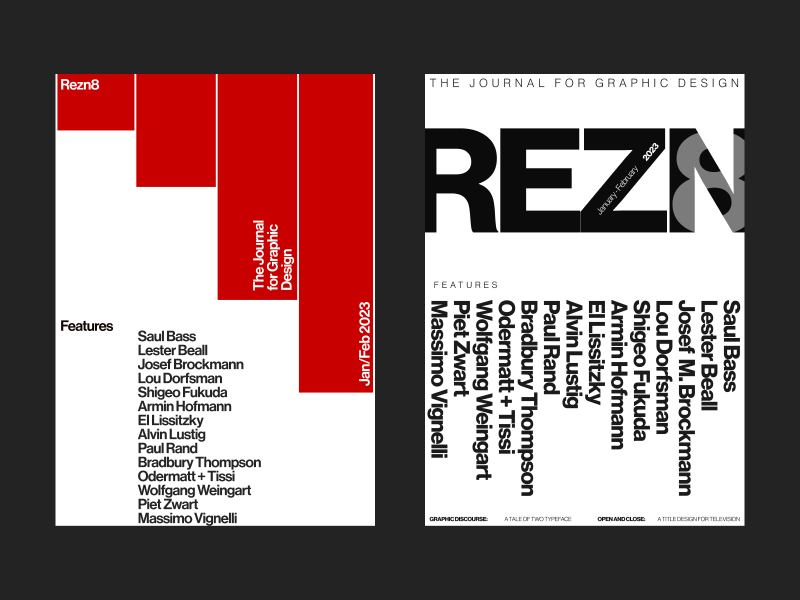
Challenges
Turning the poster into a functional site was already a challenge, but learning JavaScript on the fly to bring motion into the experience pushed me even further.
The biggest challenge, though, was researching and presenting accurate information about the legendary designers featured. Some had very little online presence, so I had to dive deep into design history to get the details right.
Personal notes
REZN-8 holds a special place in my heart. It completely changed how I see layout, grids, and type — it was the project that shifted my design brain forever. Shoutout to Chris Do and TheFutur’s Typography 01 course, which sparked the whole thing.
Live Site Link: https://rezn8.webflow.io/
Notable Explorations & Projects
Blacksmith Collective
(Webflow Template) Shameless plug 🫠
Live Site Link: https://blacksmith-sbj.webflow.io/
Velthari
Live Site Link: https://velthari.webflow.io/
Velvet Blues
Background
I didn’t start out as a designer, at least not in the traditional sense. My early work was in a marketing agency where I handled everything from FB ad graphics to SEO landing pages and WordPress articles. It wasn’t glamorous, but it gave me a foundation in how digital systems work.
Then I stumbled across Webflow — and everything changed. I got completely hooked on web design, especially sites with rich motion and interaction.
That moment pushed me to quit the agency world and start my own studio. Since then, I’ve been building expressive, story-driven websites for creatives and design-forward brands, blending design, motion, and development into something that feels personal and intentional.
Design Philosophy
I’ve always leaned toward minimal design paired with bold, heavy type. To me, you don’t need a lot to make something striking, just the right balance of restraint and intention. If the typography is solid and the layout is thoughtful, even the simplest design can carry emotional weight. I focus on clarity, rhythm, and a strong visual pulse — letting motion, space, and type do the heavy lifting.
Tools and Techniques
- Figma for most of the design work
- Webflow for front-end development and CMS integration
- GSAP for all things motion and interaction
- Cursor for dev support (because I wouldn’t call myself a “real dev,” but I make it work)
Inspiration
I pull inspiration from a lot of places — music, films, anime — especially the ones that are crafted with insane attention to detail. I’ve always admired how much intention goes into those worlds. There’s so much to steal from them — not just visually, but conceptually and emotionally. I’m also inspired by work that feels personal, raw, and beautifully uncompromising.
Future Goals
My main goal is to keep attracting work that aligns with the way I see and do things. I’m not chasing volume — I just want to keep collaborating with people who value design, story, and craft as much as I do. I’m also interested in exploring more personal projects, maybe even merging design with philosophy, fitness, or writing — things that feel more like extensions of who I am, not just what I do.
Final Thoughts
Learn from the past, embrace the present moment, and look into the future. You only live once, do what makes you happy and what feels right for you.
Contact Info
I’m mostly active on LinkedIn, X (Twitter), and occasionally Instagram.
Instagram: @bamojk
LinkedIn: https://www.linkedin.com/in/bamoj/
X (Twitter): https://x.com/bamojk
Website: bamoj.com